Lead2pass 2018 100% Valid 200-125 Dumps Guarantee 100% Pass 200-125 Certification Exam:
https://www.lead2pass.com/200-125.html
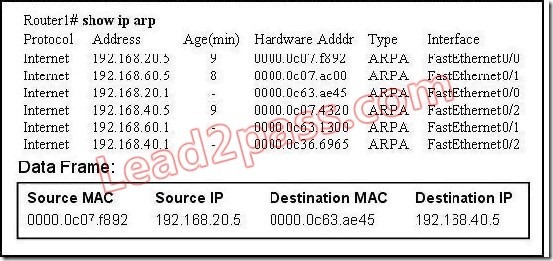
QUESTION 1
Refer to the exhibit. What will Router1 do when it receives the data frame shown? (Choose three.)
A. Router1 will strip off the source MAC address and replace it with the MAC address 0000.0c36.6965.
B. Router1 will strip off the source IP address and replace it with the IP address 192.168.40.1.
C. Router1 will strip off the destination MAC address and replace it with the MAC address 0000.0c07.4320.
D. Router1 will strip off the destination IP address and replace it with the IP address of 192.168.40.1.
E. Router1 will forward the data packet out interface FastEthernet0/1.
F. Router1 will forward the data packet out interface FastEthernet0/2.
Answer: ACF
Explanation:
Remember, the source and destination MAC changes as each router hop along with the TTL being decremented but the source and destination IP address remain the same from source to destination.
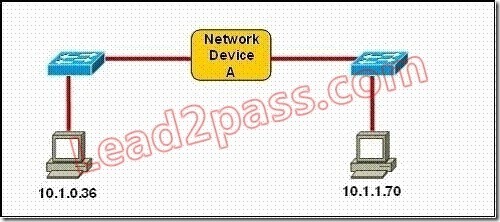
QUESTION 2
Refer to the exhibit. Which three statements correctly describe Network Device A? (Choose three.)
A. With a network wide mask of 255.255.255.128, each interface does not require an IP address.
B. With a network wide mask of 255.255.255.128, each interface does require an IP address on a
unique IP subnet.
C. With a network wide mask of 255.255.255.0, must be a Layer 2 device for the PCs to communicate
with each other.
D. With a network wide mask of 255.255.255.0, must be a Layer 3 device for the PCs to communicate
with each other.
E. With a network wide mask of 255.255.254.0, each interface does not require an IP address.
Answer: BDE
Explanation:
If Subnet Mask is 255.255.255.128 the hosts vary from x.x.x.0 – x.x.x.127 & x.x.x.128- x.x.x.255,so the IP Addresses of 2 hosts fall in different subnets so each interface needs an IP an address so that they can communicate each other.
If Subnet Mask is 255.255.255.0 the 2 specified hosts fall in different subnets so they need a Layer 3 device to communicate.
If Subnet Mask is 255.255.254.0 the 2 specified hosts are in same subnet so are in network address and can be accommodated in same Layer 2 domain and can communicate with each other directly using the Layer 2 address.
QUESTION 3
Which layer in the OSI reference model is responsible for determining the availability of the receiving program and checking to see if enough resources exist for that communication?
A. transport
B. network
C. presentation
D. session
E. application
Answer: E
Explanation:
This question is to examine the OSI reference model. The Application layer is responsible for identifying and establishing the availability of the intended communication partner and determining whether sufficient resources for the intended communication exist.
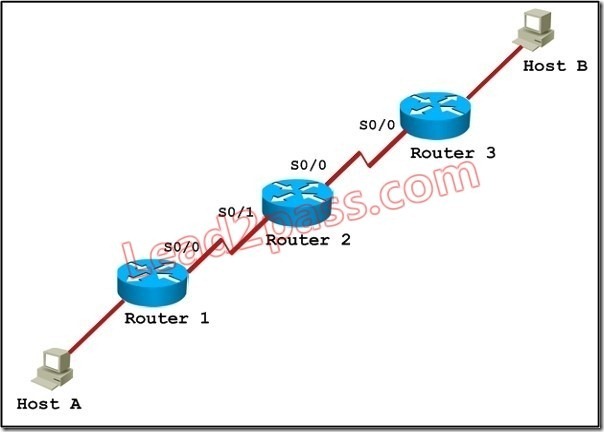
QUESTION 4
Refer to the exhibit. Host A pings interface S0/0 on router 3. What is the TTL value for that ping?
A. 252
B. 253
C. 254
D. 255
Answer: B
Explanation:
From the CCNA ICND2 Exam book: “Routers decrement the TTL by 1 every time they forward a packet; if a router decrements the TTL to 0, it throws away the packet. This prevents packets from rotating forever.” I want to make it clear that before the router forwards a packet, the TTL is still remain the same. For example in the topology above, pings to S0/1 and S0/0 of Router 2 have the same TTL.
QUESTION 5
Which of the following describes the roles of devices in a WAN? (Choose three.)
A. A CSU/DSU terminates a digital local loop.
B. A modem terminates a digital local loop.
C. A CSU/DSU terminates an analog local loop.
D. A modem terminates an analog local loop.
E. A router is commonly considered a DTE device.
F. A router is commonly considered a DCE device.
Answer: ADE
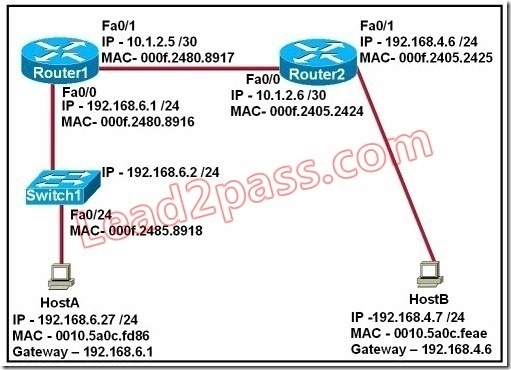
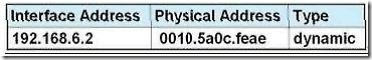
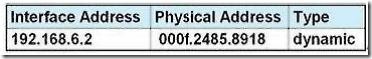
QUESTION 6
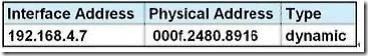
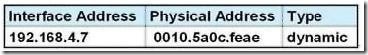
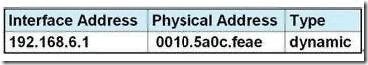
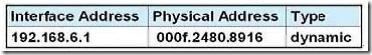
Refer to the exhibit. Refer to the exhibit. After HostA pings HostB, which entry will be in the ARP cache of HostA to support this transmission?
Answer: A
Explanation:
When a host needs to reach a device on another subnet, the ARP cache entry will be that of the Ethernet address of the local router (default gateway) for the physical MAC address. The destination IP address will not change, and will be that of the remote host (HostB).
QUESTION 7
A network administrator is verifying the configuration of a newly installed host by establishing an FTP connection to a remote server. What is the highest layer of the protocol stack that the network administrator is using for this operation?
A. application
B. presentation
C. session
D. transport
E. internet
F. data link
Answer: A
Explanation:
FTP belongs to Application layer and it is also the highest layer of the OSI model.
QUESTION 8
A network interface port has collision detection and carrier sensing enabled on a shared twisted pair network. From this statement, what is known about the network interface port?
A. This is a 10 Mb/s switch port.
B. This is a 100 Mb/s switch port.
C. This is an Ethernet port operating at half duplex.
D. This is an Ethernet port operating at full duplex.
E. This is a port on a network interface card in a PC.
Answer: C
Explanation:
Modern Ethernet networks built with switches and full-duplex connections no longer utilize CSMA/CD. CSMA/CD is only used in obsolete shared media Ethernet (which uses repeater or hub).
QUESTION 9
A receiving host computes the checksum on a frame and determines that the frame is damaged. The frame is then discarded. At which OSI layer did this happen?
A. session
B. transport
C. network
D. data link
E. physical
Answer: D
Explanation:
The Data Link layer provides the physical transmission of the data and handles error notification, network topology, and flow control. The Data Link layer formats the message into pieces, each called a data frame, and adds a customized header containing the hardware destination and source address. Protocols Data Unit (PDU) on Datalink layer is called frame. According to this question the frame is damaged and discarded which will happen at the Data Link layer.
QUESTION 10
Which of the following correctly describe steps in the OSI data encapsulation process? (Choose two.)
A. The transport layer divides a data stream into segments and may add reliability and flow control information.
B. The data link layer adds physical source and destination addresses and an FCS to the segment.
C. Packets are created when the network layer encapsulates a frame with source and destination host
addresses and protocol-related control information.
D. Packets are created when the network layer adds Layer 3 addresses and control information to a segment.
E. The presentation layer translates bits into voltages for transmission across the physical link.
Answer: AD
Explanation:
The Application Layer (Layer 7) refers to communications services to applications and is the interface between the network and the application. Examples include. Telnet, HTTP, FTP, Internet browsers, NFS, SMTP gateways, SNMP, X.400 mail, and FTAM.
The Presentation Layer (Layer 6) defining data formats, such as ASCII text, EBCDIC text, binary, BCD, and JPEG. Encryption also is defined as a presentation layer service. Examples include. JPEG, ASCII, EBCDIC, TIFF, GIF, PICT, encryption, MPEG, and MIDI.
The Session Layer (Layer 5) defines how to start, control, and end communication sessions. This includes the control and management of multiple bidirectional messages so that the application can be notified if only some of a series of messages are completed. This allows the presentation layer to have a seamless view of an incoming stream of data. The presentation layer can be presented with data if all flows occur in some cases. Examples include. RPC, SQL, NFS, NetBios names, AppleTalk ASP, and DECnet SCP
The Transport Layer (Layer 4) defines several functions, including the choice of protocols. The most important Layer 4 functions are error recovery and flow control. The transport layer may provide for retransmission, i.e., error recovery, and may use flow control to prevent unnecessary congestion by attempting to send data at a rate that the network can accommodate, or it might not, depending on the choice of protocols. Multiplexing of incoming data for different flows to applications on the same host is also performed. Reordering of the incoming data stream when packets arrive out of order is included. Examples include. TCP, UDP, and SPX.
The Network Layer (Layer 3) defines end-to-end delivery of packets and defines logical addressing to accomplish this. It also defines how routing works and how routes are learned; and how to fragment a packet into smaller packets to accommodate media with smaller maximum transmission unit sizes. Examples include. IP, IPX, AppleTalk DDP, and ICMP. Both IP and IPX define logical addressing, routing, the learning of routing information, and end-to-end delivery rules. The IP and IPX protocols most closely match the OSI network layer (Layer 3) and are called Layer 3 protocols because their functions most closely match OSI’s Layer 3.
The Data Link Layer (Layer 2) is concerned with getting data across one particular link or medium.
The data link protocols define delivery across an individual link. These protocols are necessarily concerned with the type of media in use. Examples includE. IEEE 802.3/802.2, HDLC, Frame Relay, PPP, FDDI, ATM, and IEEE 802.5/802.2.
200-125 dumps full version (PDF&VCE): https://www.lead2pass.com/200-125.html
Large amount of free 200-125 exam questions on Google Drive: https://drive.google.com/open?id=0B3Syig5i8gpDM0s1aXlFTXBWdGM
You may also need:
100-105 exam dumps: https://drive.google.com/open?id=0B3Syig5i8gpDdDNkZEswTDRMaVE
200-105 exam dumps: https://drive.google.com/open?id=0B3Syig5i8gpDX09LZEFNYnpfM2c