[PDF&VCE] Lead2pass Offering Free 300-207 Dumps Files For Free Downloading By 300-207 Exam Candidates (61-80)
2016 October Cisco Official New Released 300-207 Dumps in Lead2pass.com! 100% Free Download! 100% Pass Guaranteed! Are you interested in successfully completing the Cisco 300-207 Certification Then start to earning Salary? Lead2pass has leading edge developed Cisco exam questions that will ensure you pass this 300-207 exam! Lead2pass delivers you the most accurate, current and latest updated 300-207 Certification exam questions and available with a 100% money back guarantee promise! Following questions and answers are all new published by Cisco Official Exam Center: http://www.lead2pass.com/300-207.html 3 1 QUESTION 61
Hotspot Questions 
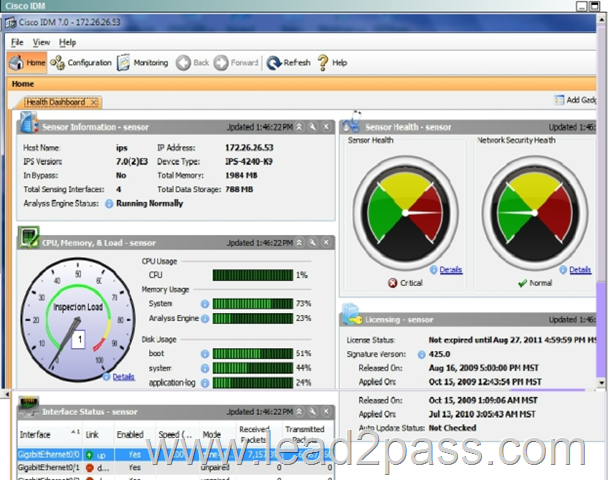
Which three statements about the Cisco IPS appliance configurations are true? (Choose three.)
A. The maximum number of denied attackers is set to 10000.
B. The block action duraton is set to 3600 seconds.
C. The Meta Event Generator is globally enabled.
D. Events Summarization is globally disabled.
E. Threat Rating Adjustment is globally disabled. Answer: ABC QUESTION 62
Hotspot Questions
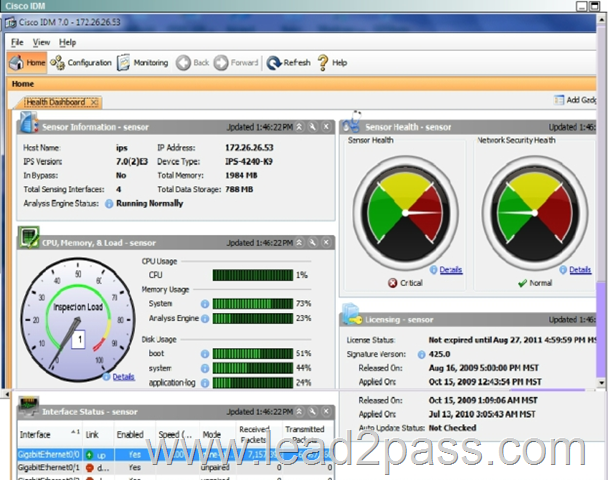
What is the status of OS Identification? A. It is only enabled to identify "Cisco IOS" OS using statically mapped OS fingerprinting
B. OS mapping information will not be used for Risk Rating calculations.
C. It is configured to enable OS mapping and ARR only for the 10.0.0.0/24 network.
D. It is enabled for passive OS fingerprinting for all networks. Answer: D
Explanation:
Understanding Passive OS Fingerprinting Passive OS fingerprinting lets the sensor determine the OS that hosts are running. The sensor analyzes network traffic between hosts and stores the OS of these hosts with their IP addresses. The sensor inspects TCP SYN and SYNACK packets exchanged on the network to determine the OS type. The sensor then uses the OS of the target host OS to determine the relevance of the attack to the victim by computing the attack relevance rating component of the risk rating. Based on the relevance of the attack, the sensor may alter the risk rating of the alert for the attack and/or the sensor may filter the alert for the attack. You can then use the risk rating to reduce the number of false positive alerts (a benefit in IDS mode) or definitively drop suspicious packets (a benefit in IPS mode). Passive OS fingerprinting also enhances the alert output by reporting the victim OS, the source of the OS identification, and the relevance to the victim OS in the alert. Passive OS fingerprinting consists of three components:
Passive OS learning occurs as the sensor observes traffic on the network.
Based on the characteristics of TCP SYN and SYNACK packets, the sensor makes a determination of the OS running on the host of the source IP address.
User-configurable OS identification You can configure OS host mappings, which take precedence over learned OS mappings.
Computation of attack relevance rating and risk rating QUESTION 63
Lab Simulation
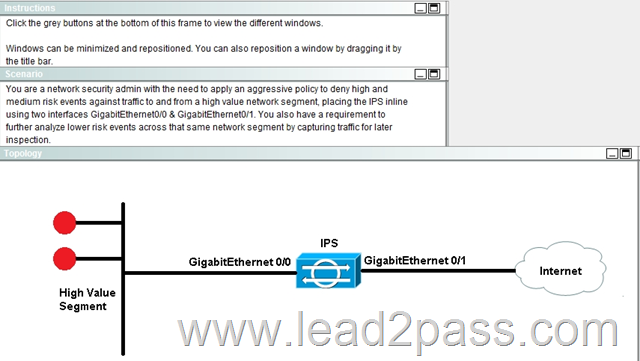
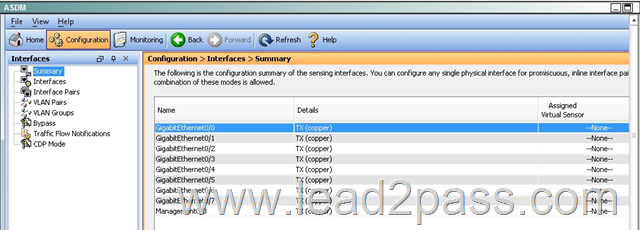
Answer:
Steps are in Explanation below:
First, enable the Gig 0/0 and Gig 0/1 interfaces:
Second, create the pair under the "interface pairs" tab:
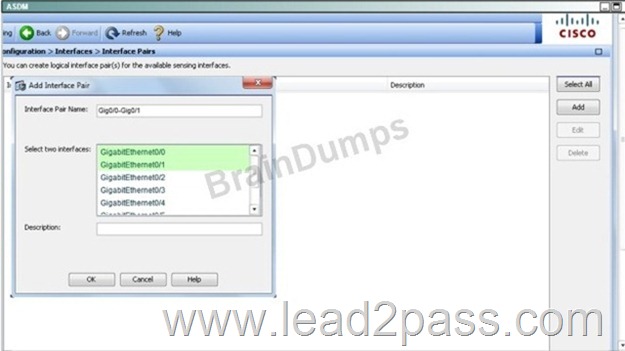
Then, apply the HIGHRISK action rule to the newly created interface pair:
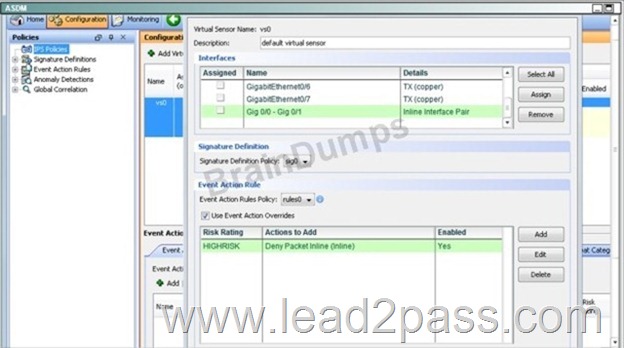
Then apply the same for the MEDIUMRISK traffic (deny attacker inline)
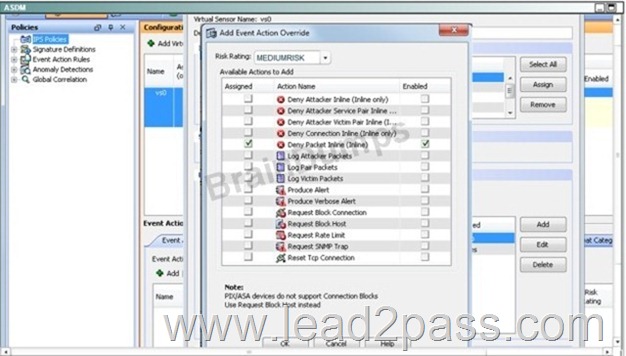
Finally. Log the packets for the LOWRICK event:
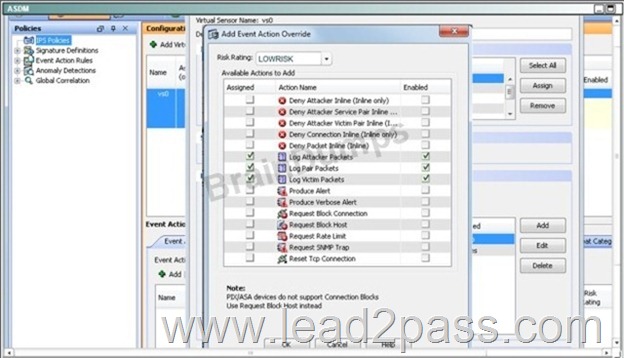
When done it should look like this:
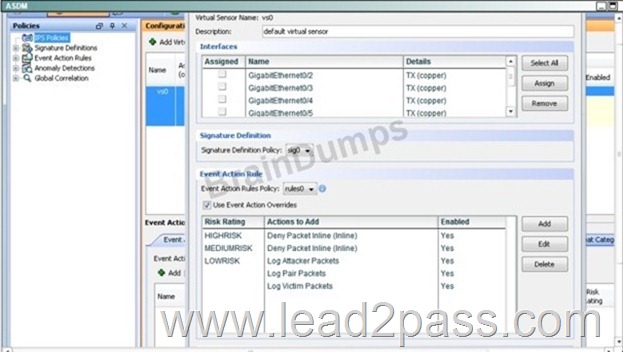
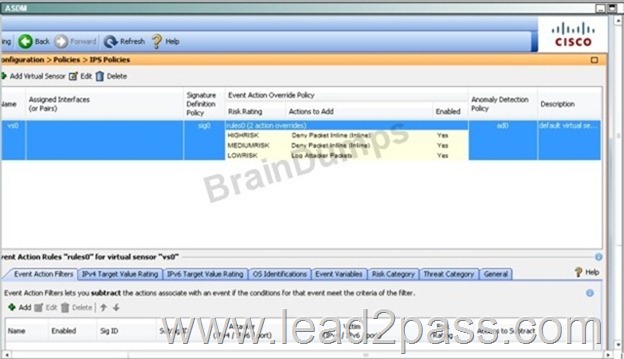 QUESTION 64
During initial configuration, the Cisco ASA can be configured to drop all traffic if the ASA CX SSP fails by using which command in a policy-map? A. cxsc fail
B. cxsc fail-close
C. cxsc fail-open
D. cxssp fail-close Answer: B QUESTION 65
A network engineer may use which three types of certificates when implementing HTTPS decryption services on the ASA CX? (Choose three.) A. Self Signed Server Certificate
B. Self Signed Root Certificate
C. Microsoft CA Server Certificate
D. Microsoft CA Subordinate Root Certificate
E. LDAP CA Server Certificate
F. LDAP CA Root Certificate
G. Public Certificate Authority Server Certificate
H. Public Certificate Authority Root Certificate Answer: BDF QUESTION 66
Cisco's ASA CX includes which two URL categories? (Choose two.) A. Proxy Avoidance
B. Dropbox
C. Hate Speech
D. Facebook
E. Social Networking
F. Instant Messaging and Video Messaging Answer: CE QUESTION 67
A Cisco Web Security Appliance's policy can provide visibility and control of which two elements? (Choose two.) A. Voice and Video Applications
B. Websites with a reputation between -100 and -60
C. Secure websites with certificates signed under an unknown CA
D. High bandwidth websites during business hours Answer: CD QUESTION 68
Which Cisco Web Security Appliance design requires minimal change to endpoint devices? A. Transparent Mode
B. Explicit Forward Mode
C. Promiscuous Mode
D. Inline Mode Answer: A QUESTION 69
What step is required to enable HTTPS Proxy on the Cisco Web Security Appliance? A. Web Security Manager HTTPS Proxy click Enable
B. Security Services HTTPS Proxy click Enable
C. HTTPS Proxy is enabled by default
D. System Administration HTTPS Proxy click Enable Answer: B QUESTION 70
Which two statements about Cisco Cloud Web Security functionality are true? (Choose two.) A. It integrates with Cisco Integrated Service Routers.
B. It supports threat avoidance and threat remediation.
C. It extends web security to the desktop, laptop, and PDA.
D. It integrates with Cisco ASA Firewalls. Answer: AD QUESTION 71
Which Cisco Cloud Web Security tool provides URL categorization? A. Cisco Dynamic Content Analysis Engine
B. Cisco ScanSafe
C. ASA Firewall Proxy
D. Cisco Web Usage Control Answer: A QUESTION 72
Which three functions can Cisco Application Visibility and Control perform? (Choose three.) A. Validation of malicious traffic
B. Traffic control
C. Extending Web Security to all computing devices
D. Application-level classification
E. Monitoring
F. Signature tuning Answer: BDE QUESTION 73
Which two options are features of the Cisco Email Security Appliance? (Choose two.) A. Cisco Anti-Replay Services
B. Cisco Destination Routing
C. Cisco Registered Envelope Service
D. Cisco IronPort SenderBase Network Answer: CD QUESTION 74
What is the authentication method for an encryption envelope that is set to medium security? A. The recipient must always enter a password, even if credentials are cached.
B. A password is required, but cached credentials are permitted.
C. The recipient must acknowledge the sensitivity of the message before it opens.
D. The recipient can open the message without authentication. Answer: B QUESTION 75
What is the default antispam policy for positively identified messages? A. Drop
B. Deliver and Append with [SPAM]
C. Deliver and Prepend with [SPAM]
D. Deliver and Alternate Mailbox Answer: C QUESTION 76
Which five system management protocols are supported by the Cisco Intrusion Prevention System? (Choose five.) A. SNMPv2c
B. SNMPv1
C. SNMPv2
D. SNMPv3
E. Syslog
F. SDEE
G. SMTP Answer: ABCFG QUESTION 77
Which four statements are correct regarding management access to a Cisco Intrusion Prevention System? (Choose four.) A. The Telnet protocol is enabled by default
B. The Telnet protocol is disabled by default
C. HTTP is enabled by default
D. HTTP is disabled by default
E. SSH is enabled by default
F. SSH is disabled by default
G. HTTPS is enabled by default
H. HTTPS is disabled by default Answer: BDEG QUESTION 78
Which two GUI options display users' activity in Cisco Web Security Appliance? (Choose two.) A. Web Security Manager Identity Identity Name
B. Security Services Reporting
C. Reporting Users
D. Reporting Reports by User Location Answer: CD QUESTION 79
The security team needs to limit the number of e-mails they receive from the Intellishield Alert Service. Which three parameters can they adjust to restrict alerts to specific product sets? (Choose three.) A. Vendor
B. Chassis/Module
C. Device ID
D. Service Contract
E. Version/Release
F. Service Pack/Platform Answer: AEF QUESTION 80
A Cisco AnyConnect user profile can be pushed to the PC of a remote user from a Cisco ASA. Which three user profile parameters are configurable? (Choose three.) A. Backup Server list
B. DTLS Override
C. Auto Reconnect
D. Simultaneous Tunnels
E. Connection Profile Lock
F. Auto Update Answer: ACF All Cisco 300-207 exam questions are the new checked and updated! In recent years, the 300-207 certification has become a global standard for many successful IT companies. Want to become a certified Cisco professional? Download Lead2pass 2016 latest released 300-207 exam dumps full version and pass 300-207 100%! 300-207 new questions on Google Drive: https://drive.google.com/open?id=0B3Syig5i8gpDM2V5bnM0dTVhYjg 2 2016 Cisco 300-207 exam dumps (All 251 Q&As) from Lead2pass: http://www.lead2pass.com/300-207.html 3 1 [100% Exam Pass Guaranteed]
|













