[PDF&VCE] Lead2pass Free 200-125 Exam Questions Download 100% Pass 200-125 Exam (261-285)
2016 September Cisco Official New Released 200-125 Dumps in Lead2pass.com! 100% Free Download! 100% Pass Guaranteed! You can prepare for Cisco 200-125 exam with little effort because Lead2pass is now at your service to act as a guide to pass Cisco 200-125 exam. Our Cisco 200-125 braindumps are rich in variety. We offer Cisco 200-125 PDF dumps and Cisco 200-125 VCE. Both are the newest version. Following questions and answers are all new published by Cisco Official Exam Center: http://www.lead2pass.com/200-125.html 3 1 QUESTION 261
Lab Simulation Question - CLI
Central Florida Widgets recently installed a new router in their office. Complete the network installation by performing the initial router configurations and configuring R1PV2 routing using the router command line interface (CLI) on the RC.
Configure the router per the following requirements:
- Name of the router is R2
- Enable.secret password is cisco
- The password to access user EXEC mode using the console is cisco2
- The password to allow telnet access to the router is cisco3
IPV4 addresses mast be configured as follows:
- Ethernet network 209.165.201.0/27 - router has fourth assignable host address in subnet
- Serial network is 192.0.2.176/28 - router has last assignable host address in the subnet.
- Interfaces should be enabled.
- Router protocol is RIPV2
Attention:
In practical examinations, please note the following, the actual information will prevail.
1. Name or the router is xxx
2. EnablE. secret password is xxx
3. Password In access user EXEC mode using the console is xxx
4. The password to allow telnet access to the router is xxx
5. IP information 

Answer:
Step 1:
Click on the console host, you will get a pop-up screen CLI of Router.
Router>
Configure the new router as per the requirements provided in Lab question
Requirement 1:
Name of the router is R2
Step 2:
To change the hostname of the router to R2 follow the below steps:
Router>
Router>enable
Router#configure terminal
Router(config)#hostname R2
R2(config)#
Requirement 2:
Enable-secret password is cisco1
Step 3:
To set the enable secret password to cisco1 use the following command
R2(config)#enable secret cisco1
Requirement 3:
The password to access user EXEC mode using the console is cisco2
Step 4:
We need to configure the line console 0 with the password cisco2
Also remember to type login command after setting up the password on line con 0 which allows router to accept logins via console.
R2(config)#line con 0
R2(config-line)#password cisco2
R2(config-line)#login
R2(config-line)#exit
R2(config)#
Requirement 4:
The password to allow telnet access to the router is cisco3
Step 5:
To allow telnet access we need to configure the vty lines 0 4 with the password cisco3
Also remember to type login command after setting up the password on line vty 0 4 which allows router to accept logins via telnet.
R2(config)#line vty 0 4
R2(config-line)#password cisco3
R2(config-line)#login
R2(config-line)#exit
R2(config)#
Requirement 5:
(5.1) Ethernet network 209.165.201.0 /27 - Router has the fourth assignable host address in subnet.
(5.2) Serial Network is 192.0.2.176 /28 - Router has the last assignable host address in subnet.
Step 6:
Ethernet network 209.165.201.0 /27 - Router has the fourth assignable host address in subnet.
Ethernet Interface on router R2 is Fast Ethernet 0/0 as per the exhibit
First we need to identify the subnet mask
Network: 209.165.201.0 /27
Subnet mask: /27: 27 bits = 8 + 8 + 8 + 3
=8(bits).8(bits).8(bits) .11100000 (3bits)
=255.255.255.11100000
=11100000 = 128+64+32+0+0+0+0+0
= 224
Subnet mask: 255.255.255.224
Different subnet networks and there valid first and last assignable host address range for above subnet mask are
Subnet Networks :::::: Valid Host address range :::::: Broadcast address
209.165.201.0 :::::: 209.165.201.1 - 209.165.201.30 ::::: 209.165.201.31
209.165.201.32 :::::: 209.165.201.33 - 209.165.201.62 ::::: 209.165.201.63
209.165.201.64 :::::: 209.165.201.65 - 209.165.201.94 :::::: 209.165.201.95
209.165.201.96 :::::: 209.165.201.97 - 209.165.201.126 :::::: 209.165.201.127
209.165.201.128 :::::: 209.165.201.129 - 209.165.201.158 :::::: 209.165.201.159
209.165.201.160 :::::: 209.165.201.161 - 209.165.201.190 :::::: 209.165.201.191
209.165.201.192 :::::: 209.165.201.193 - 209.165.201.222 :::::: 209.165.201.223
209.165.201.224 :::::: 209.165.201.225 - 209.165.201.254 :::::: 209.165.201.255
Use above table information for network 209.165.201.0 /27 to identify
First assignable host address: 209.165.201.1
Last assignable host address: 209.165.201.30
Fourth assignable host address: 209.165.201.4
This IP address (209.165.201.4) which we need to configure on Fast Ethernet 0/0 of the router using the subnet mask 255.255.255.224
R2(config)#interface fa 0/0
R2(config-if)#ip address 209.165.201.4 255.255.255.224
Requirement 6:
To enable interfaces
Use no shutdown command to enable interfaces
R2(config-if)#no shutdown
R2(config-if)#exit
Step 7:
Serial Network is 192.0.2.176 /28 - Router has the last assignable host address in subnet.
Serial Interface on R2 is Serial 0/0/0 as per the exhibit
First we need to identify the subnet mask
Network: 192.0.2.176 /28
Subnet mask: /28: 28bits = 8bits+8bits+8bits+4bits
=8(bits).8(bits).8(bits) .11110000 (4bits)
=255.255.255.11100000
=11100000 = 128+64+32+16+0+0+0+0
= 240
Subnet mask: 255.255.255.240
Different subnet networks and there valid first and last assignable host address range for above subnet mask are
Subnet Networks ::::: Valid Host address ::::::::::: Broadcast address
192.0.2.0 :::::: 192.0.2.1 - 192.0.2.14 ::::::: 192.0.2.15
192.0.2.16 ::::::: 192.0.2.17 - 192.0.2.30 ::::::: 192.0.2.31
192.0.2.32 :::::::: 192.0.2.33 - 192.0.2.46 :::::: 192.0.2.47
192.0.2.48 :::::: 192.0.2.49 - 192.0.2.62 ::::::: 192.0.2.64
192.0.2.64 ::::::: 192.0.2.65 - 192.0.2.78 ::::::: 192.0.2.79
192.0.2.80 :::::::: 192.0.2.81 - 192.0.2.94 :::::: 192.0.2.95
192.0.2.96 :::::: 192.0.2.97 - 192.0.2.110 ::::::: 192.0.2.111
192.0.2.112 ::::::: 192.0.2.113 - 192.0.2.126 ::::::: 192.0.2.127
192.0.2.128 :::::::: 192.0.2.129 - 192.0.2.142 :::::: 192.0.2.143
192.0.2.144 :::::: 192.0.2.145 - 192.0.2.158 ::::::: 192.0.2.159
192.0.2.160 ::::::: 192.0.2.161 - 192.0.2.174 ::::::: 192.0.2.175
192.0.2.176 :::::::: 192.0.2.177 - 192.0.2.190 :::::: 192.0.2.191
and so on ….
Use above table information for network 192.0.2.176 /28 to identify
First assignable host address: 192.0.2.177
Last assignable host address: 192.0.2.190
We need to configure Last assignable host address (192.0.2.190) on serial 0/0/0 using the subnet mask 255.255.255.240
R2(config)#interface serial 0/0/0
R2(config-if)#ip address 192.0.2.190 255.255.255.240
Requirement 6:
To enable interfaces
Use no shutdown command to enable interfaces
R2(config-if)#no shutdown
R2(config-if)#exit
Requirement 7:
Router protocol is RIPv2
Step 8:
Need to enable RIPv2 on router and advertise its directly connected networks
R2(config)#router rip
To enable RIP v2 routing protocol on router use the command version 2
R2(config-router)#version 2
Optional: no auto-summary (Since LAB networks do not have discontinuous networks)
RIP v2 is classless, and advertises routes including subnet masks, but it summarizes routes by default.
So the first things we need to do when configuring RIP v2 is turn off auto-summarization with the router command no auto-summary if you must perform routing between disconnected subnets.
R2 (config-router) # no auto-summary
Advertise the serial 0/0/0 and fast Ethernet 0/0 networks into RIP v2 using network command
R2(config-router)#network 192.0.2.176
R2(config-router)#network 209.165.201.0
R2(config-router)#end
Step 9:
Important please do not forget to save your running-config to startup-config
R2# copy running-config startup-config
QUESTION 262
Lab Simulation Question - ACL-4
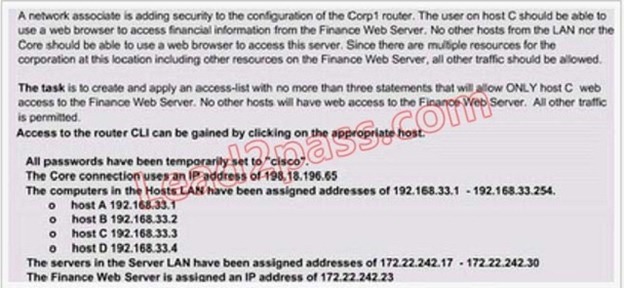
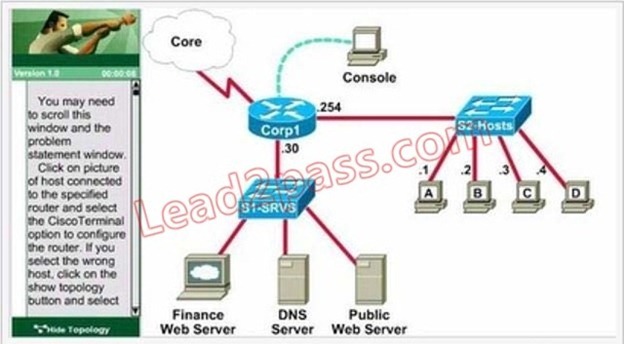
Answer:
Corp1>enable
Corp1#configure terminal
Corp1(config)#access-list 100 permit tcp host 192.168.33.3 host 172.22.242.23 eq 80
Corp1(config)#access-list 100 deny tcp any host 172.22.242.23 eq 80
Corp1(config)#access-list 100 permit ip any any
Corp1(config)#interface fa 0/1 sh ip int brief
Corp1(config-if)#ip access-group 100 out
Corp1(config-if)#end
Corp1#copy running-config startup-config
Explanation:
Select the console on Corp1 router
Configuring ACL
Corp1>enable
Corp1#configure terminal
Comment: To permit only Host C (192.168.33.3){source addr} to access finance server address (172.22.242.23) {destination addr} on port number 80 (web)
Corp1(config)#access-list 100 permit tcp host 192.168.33.3 host 172.22.242.23 eq 80
Comment: To deny any source to access finance server address (172.22.242.23) {destination addr} on port number 80 (web)
Corp1(config)#access-list 100 deny tcp any host 172.22.242.23 eq 80
Comment: To permit ip protocol from any source to access any destination because of the implicit deny any any statement at the end of ACL.
Corp1(config)#access-list 100 permit ip any any
Applying the ACL on the Interface
Comment: Check show ip interface brief command to identify the interface type and number by checking the IP address configured.
Corp1(config)#interface fa 0/1
If the ip address configured already is incorrect as well as the subnet mask. this should be corrected in order ACL to work type this commands at interface mode :
no ip address 192.x.x.x 255.x.x.x (removes incorrect configured ipaddress and subnet mask) Configure Correct IP Address and subnet mask:
ip address 172.22.242.30 255.255.255.240 ( range of address specified going to server is given as 172.22.242.17 - 172.22.242.30 )
Comment: Place the ACL to check for packets going outside the interface towards the finance web server.
Corp1(config-if)#ip access-group 100 out
Corp1(config-if)#end
Important: To save your running config to startup before exit.
Corp1#copy running-config startup-config
Verifying the Configuration:
Step1: show ip interface brief command identifies the interface on which to apply access list. Step2: Click on each host A,B,C & D . Host opens a web browser page , Select address box of the web browser and type the ip address of finance web server(172.22.242.23) to test whether it permits /deny access to the finance web Server .
Step 3: Only Host C (192.168.33.3) has access to the server . If the other host can also access then maybe something went wrong in your configuration . check whether you configured correctly and in order.
Step 4: If only Host C (192.168.33.3) can access the Finance Web Server you can click on NEXT button to successfully submit the ACL SIM. QUESTION 263
Lab Simulation Question - ACL-2
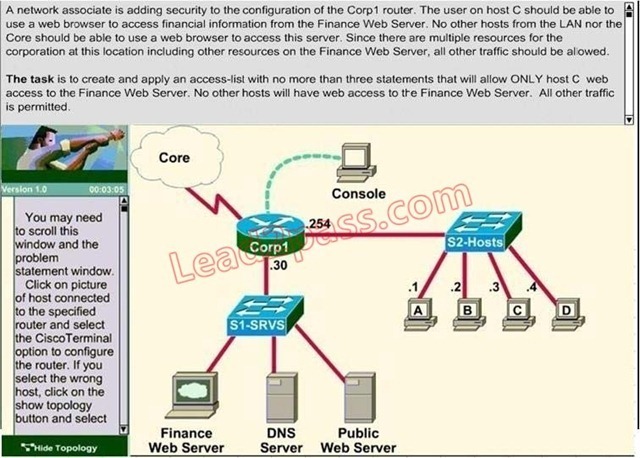

Answer:
Corp1#conf t
Corp1(config)# access-list 128 permit tcp host 192.168.240.1 host 172.22.141.26 eq www Corp1(config)# access-list 128 deny tcp any host 172.22.141.26 eq www
Corp1(config)# access-list 128 permit ip any any
Corp1(config)#int fa0/1
Corp1(config-if)#ip access-group 128 out
Corp1(config-if)#end
Corp1#copy run startup-config QUESTION 264
Lab Simulation Question - ACL-3
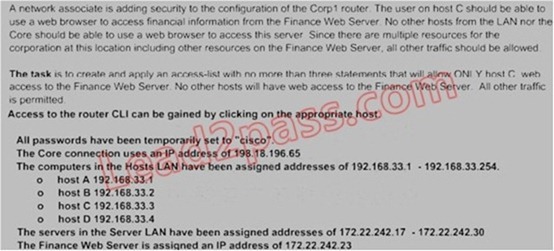
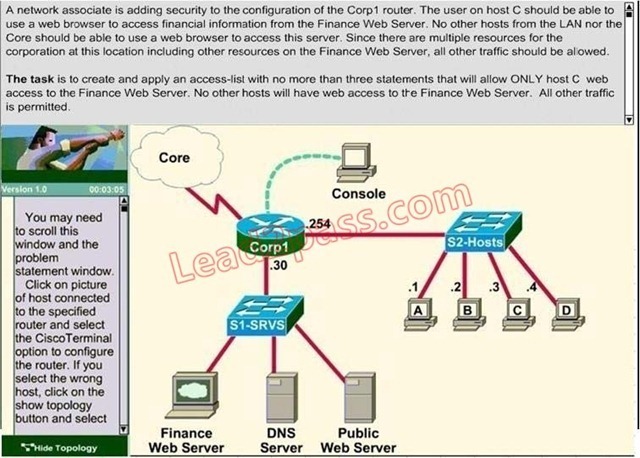
Answer:
Corp1>enable
Corp1#configure terminal
Corp1(config)#access-list 100 permit tcp host 192.168.33.3 host 172.22.242.23 eq 80
Corp1(config)#access-list 100 deny tcp 192.168.33.0 0.0.0.255 host 172.22.242.23 eq 80
Corp1(config)#access-list 100 permit ip any any
Corp1(config)#interface fa 0/1 sh ip int brief
Corp1(config-if)#ip access-group 100 out
Corp1(config-if)#end
Corp1#copy running-config startup-config
Explanation:
Select the console on Corp1 router
Configuring ACL
Corp1 >enable
Corp1#configure terminal
comment: To permit only Host C (192.168. 33. 3){source addr} to access finance server address (172.22. 242. 23){destination addr} on port number 80 (web)
Corp1(config)#access-list 100 permit tcp host 192.168.33.3 host 172.22.242.23 eq 80
Comment: To deny any source to access finance server address (172. 22. 242. 23) {destination addr} on port number 80 (web)
Corp1(config)#access-list 100 deny tcp any host 172.22.242.23 eq 80
Comment: To permit ip protocol from any source to access any destination because of the implicit deny any any statement at the end of ACL.
Corp1(config)#access-list 100 permit ip any any
Applying the ACL on the Interface
comment: Check show ip interface brief command to identify the interface type and number by checking the IP address configured.
Corp1(config)#interface fa 0/1
If the ip address configured already is incorrect as well as the subnet mask, this should be corrected in order ACL to work type this commands at interface mode :
no ip address 192. x. x. x 255. x. x. x (removes incorrect configured ip address and subnet mask) Configure Correct IP Address and subnet mask:
ip address 172. 22. 242. 30 255. 255. 255. 240 (range of address specified going to server is given as 172. 22. 242. 17-172. 22. 242. 30 )
Comment: Place the ACL to check for packets going outside the interface towards the finance web server.
Corp1(config-if)#ip access-group 100 out
Corp1(config-if)#end
Important: To save your running config to startup before exit.
Corp1#copy running-config startup- config
Verifying the Configuration:
Step1: show ip interface brief command identifies the interface on which to apply access list. Step2: Click on each host A,B,C & D. Host opens a web browser page, Select address box of the web browser and type the ip address of finance web server(172. 22. 242. 23) to test whether it permits /deny access to the finance web Server.
Step 3: Only Host C (192.168. 33. 3) has access to the server. If the other host can also access then maybe something went wrong in your configuration check whether you configured correctly and in order.
Step 4: If only Host C (192.168. 33. 3) can access the Finance Web Server you can click on NEXT button to successfully submit the ACL SIM. QUESTION 265
Lab Simulation Question - NAT-1

A network associate is configuring a router for the weaver company to provide internet access. The ISP has provided the company six public IP addresses of 198.18.184.105 198.18.184.110. The company has 14 hosts that need to access the internet simultaneously. The hosts in the company LAN have been assigned private space addresses in the range of 192.168.100.17 ?192.168.100.30.
Answer:
The company has 14 hosts that need to access the internet simultaneously but we just have 6 public IP addresses from 198.18.184.105 to 198.18.184.110/29.
Therefore we have to use NAT overload (or PAT)
Double click on the Weaver router to open it
Router>enable
Router#configure terminal
First you should change the router's name to Weaver
Router(config)#hostname Weaver
Create a NAT pool of global addresses to be allocated with their netmask.
Weaver(config)#ip nat pool mypool 198.18.184.105 198.18.184.110 netmask 255.255.255.248
Create a standard access control list that permits the addresses that are to be translated
Weaver(config)#access-list 1 permit 192.168.100.16 0.0.0.15
Establish dynamic source translation, specifying the access list that was defined in the prior step
Weaver(config)#ip nat inside source list 1 pool mypool overload
This command translates all source addresses that pass access list 1, which means a source address from 192.168.100.17 to 192.168.100.30, into an address from the pool named mypool (the pool contains addresses from 198.18.184.105 to 198.18.184.110)
Overload keyword allows to map multiple IP addresses to a single registered IP address (many-to-one) by using different ports
The question said that appropriate interfaces have been configured for NAT inside and NAT outside statements.
This is how to configure the NAT inside and NAT outside, just for your understanding:
Weaver(config)#interface fa0/0
Weaver(config-if)#ip nat inside
Weaver(config-if)#exit
Weaver(config)#interface s0/0
Weaver(config-if)#ip nat outside
Weaver(config-if)#end
Finally, we should save all your work with the following command:
Weaver#copy running-config startup-config
Check your configuration by going to "Host for testing" and type:
C :>ping 192.0.2.114
The ping should work well and you will be replied from 192.0.2.114 QUESTION 266
Lab Simulation Question - NAT-2
A network associate is configuring a router for the Weaver company to provide internet access. The ISP has provided the company six public IP addresses of 198.18.184.105 - 198.18.184.110. The company has 14 hosts that need to access the internet simultaneously. The hosts in the company LAN have been assigned private space addresses in the range of 192.168.100.17 – 192.168.100.30.
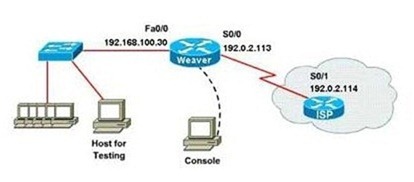
The following have already been configured on the router:
The basic router configuration
The appropriate interfaces have been configured for NAT inside and NAT outside
The appropriate static routes have also been configured (since the company will be a stub network, no routing protocol will be required.)
All passwords have been temporarily set to “cisco”
The task is to complete the NAT configuration using all IP addresses assigned by the ISP to provide internet access for the hosts in the weaver LAN. Functionality can be tested by clicking on the host provided for testing.
Configuration information:
Router name - Weaver
Inside global addresses - 198.18.184.105 – 198.18.184.110 /29
Inside local addresses - 192.168.100.17 – 192.168.100.30 /28
Number of inside hosts - 14
Answer:
Step 1: Router Name
Router>enable
Router#configure terminal
Router(config)#hostname Weaver
Weaver(config)#
Step 2: NAT Configuration
Weaver(config)#access-list 10 permit 192.168.100.16 0.0.0.15
Weaver(config)#ip nat pool mynatpool 198.18.184.105 198.18.184.110 netmask 255.255.255.248
Weaver(config)#ip nat inside source list 10 pool mynatpool overload
Weaver(config)#end
Step 3: Save Configuration
Weaver#copy run start
Verification:
We can verify the answer by pinging the ISP IP Address (192.0.2.114) from Host for testing.
Click “Host for testing”
In command prompt, type “ping 192.0.2.114”. If ping succeeded then the NAT is working properly.
Screen Shots: QUESTION 267
In a switched environment, what does the IEEE 802.1Q standard describe? A. the operation of VTP
B. a method of VLAN trunking
C. an approach to wireless LAN communication
D. the process for root bridge selection
E. VLAN pruning Answer: B
Explanation:
A broadcast domain must sometimes exist on more than one switch in the network. To accomplish this, one switch must send frames to another switch and indicate which VLAN a particular frame belongs to. On Cisco switches, a trunk link is created to accomplish this VLAN identification. ISL and IEEE 802.1Q are different methods of putting a VLAN identifier in a Layer 2 frame. The IEEE 802.1Q protocol interconnects VLANs between multiple switches, routers, and servers. With 802.1Q, a network administrator can define a VLAN topology to span multiple physical devices.
Cisco switches support IEEE 802.1Q for FastEthernet and Gigabit Ethernet interfaces. An 802.1Q trunk link provides VLAN identification by adding a 4-byte tag to an Ethernet Frame as it leaves a trunk port. QUESTION 268
What are three benefits of GLBP? (Choose three.) A. GLBP supports up to eight virtual forwarders per GLBP group.
B. GLBP supports clear text and MD5 password authentication between GLBP group members.
C. GLBP is an open source standardized protocol that can be used with multiple vendors.
D. GLBP supports up to 1024 virtual routers.
E. GLBP can load share traffic across a maximum of four routers.
F. GLBP elects two AVGs and two standby AVGs for redundancy. Answer: BDE QUESTION 269
Which three statements about HSRP operation are true? (Choose three.) A. The virtual IP address and virtual MA+K44C address are active on the HSRP Master router.
B. The HSRP default timers are a 3 second hello interval and a 10 second dead interval.
C. HSRP supports only clear-text authentication.
D. The HSRP virtual IP address must be on a different subnet than the routers' interfaces on the same LAN.
E. The HSRP virtual IP address must be the same as one of the router's interface addresses on the LAN.
F. HSRP supports up to 255 groups per interface, enabling an administrative form of load balancing. Answer: ABF
Explanation:
The virtual MAC address of HSRP version 1 is 0000.0C07.ACxx, where xx is the HSRP group number in hexadecimal based on the respective interface. For example, HSRP group 10 uses the HSRP virtual MAC address of 0000.0C07.AC0A. HSRP version 2 uses a virtual MAC address of 0000.0C9F.FXXX (XXX: HSRP group in hexadecimal) QUESTION 270
Which three statements about Syslog utilization are true? (Choose three.) A. Utilizing Syslog improves network performance.
B. The Syslog server automatically notifies the network administrator of network problems.
C. A Syslog server provides the storage space necessary to store log files without using router disk space.
D. There are more Syslog messages available within Cisco IOS than there are comparable SNMP trap messages.
E. Enabling Syslog on a router automatically enables NTP for accurate time stamping.
F. A Syslog server helps in aggregation of logs and alerts. Answer: CDF QUESTION 271
A network administrator enters the following command on a router: logging trap 3. What are three message types that will be sent to the Syslog server? (Choose three.) A. informational
B. emergency
C. warning
D. critical
E. debug
F. error Answer: BDF QUESTION 272
What is the default Syslog facility level? A. local4
B. local5
C. local6
D. local7 Answer: D QUESTION 273
What command instructs the device to timestamp Syslog debug messages in milliseconds? A. service timestamps log datetime localtime
B. service timestamps debug datetime msec
C. service timestamps debug datetime localtime
D. service timestamps log datetime msec Answer: B
Explanation:
The "service timestamps debug" command configures the system to apply a time stamp to debugging messages. The time-stamp format for datetime is MMM DD HH:MM:SS, where MMM is the month, DD is the date, HH is the hour (in 24-hour notation), MM is the minute, and SS is the second. With the additional keyword msec, the system includes milliseconds in the time stamp, in the format HH:DD:MM:SS.mmm, where .mmm is milliseconds QUESTION 274
Refer to the exhibit. What is the cause of the Syslog output messages?
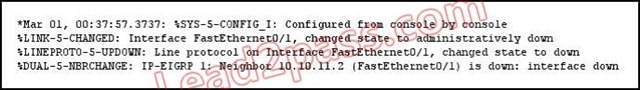 A. The EIGRP neighbor on Fa0/1 went down due to a failed link.
B. The EIGRP neighbor connected to Fa0/1 is participating in a different EIGRP process, causing the adjacency
to go down.
C. A shut command was executed on interface Fa0/1, causing the EIGRP adjacency to go down.
D. Interface Fa0/1 has become error disabled, causing the EIGRP adjacency to go down. Answer: C QUESTION 275
What are three components that comprise the SNMP framework? (Choose three.) A. MIB
B. agent
C. set
D. AES
E. supervisor
F. manager Answer: ABF QUESTION 276
What are three components that comprise the SNMP framework? (Choose three.) A. MIB
B. agent
C. set
D. AES
E. supervisor
F. manager Answer: ABF QUESTION 277
What SNMP message alerts the manager to a condition on the network? A. response
B. get
C. trap
D. capture Answer: C QUESTION 278
What authentication type is used by SNMPv2? A. HMAC-MD5
B. HMAC-SHA
C. CBC-DES
D. community strings Answer: D QUESTION 279
Which three statements about the features of SNMPv2 and SNMPv3 are true? (Choose three.) A. SNMPv3 enhanced SNMPv2 security features.
B. SNMPv3 added the Inform protocol message to SNMP.
C. SNMPv2 added the Inform protocol message to SNMP.
D. SNMPv3 added the GetBulk protocol messages to SNMP.
E. SNMPv2 added the GetBulk protocol message to SNMP.
F. SNMPv2 added the GetNext protocol message to SNMP. Answer: ACE QUESTION 280
What are three reasons to collect Netflow data on a company network? (Choose three.) A. To identify applications causing congestion.
B. To authorize user network access.
C. To report and alert link up / down instances.
D. To diagnose slow network performance, bandwidth hogs, and bandwidth utilization.
E. To detect suboptimal routing in the network.
F. To confirm the appropriate amount of bandwidth that has been allocated to each Class of Service. Answer: ADF QUESTION 281
What Netflow component can be applied to an interface to track IPv4 traffic? A. flow monitor
B. flow record
C. flow sampler
D. flow exporter Answer: A
Explanation:
Flow monitors are the Flexible NetFlow component that is applied to interfaces to perform network traffic monitoring. Flow monitors consist of a record and a cache. You add the record to the flow monitor after you create the flow monitor. The flow monitor cache is automatically created at the time the flow monitor is applied to the first interface. Flow data is collected from the network traffic during the monitoring process based on the key and nonkey fields in the record, which is configured for the flow monitor and stored in the flow monitor cache.
For example, the following example creates a flow monitor named FLOW-MONITOR-1 and enters Flexible NetFlow flow monitor configuration mode:
Router(config)# flow monitor FLOW-MONITOR-1
Router(config-flow-monitor)# QUESTION 282
What Cisco IOS feature can be enabled to pinpoint an application that is causing slow network performance? A. SNMP
B. Netflow
C. WCCP
D. IP SLA Answer: B QUESTION 283
What command visualizes the general NetFlow data on the command line? A. show ip flow export
B. show ip flow top-talkers
C. show ip cache flow
D. show mls sampling
E. show mls netflow ip Answer: C
Explanation:
The "show ip cache flow" command displays a summary of the NetFlow QUESTION 284
What are three values that must be the same within a sequence of packets for Netflow to consider them a network flow? (Choose three.) A. source IP address
B. source MAC address
C. egress interface
D. ingress interface
E. destination IP address
F. IP next-hop Answer: ADE QUESTION 285
Refer to the exhibit. A network administrator is configuring an EtherChannel between SW1 and SW2. The SW1 configuration is shown. What is the correct configuration for SW2?
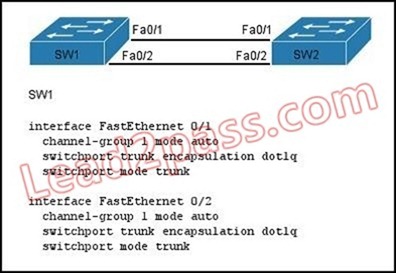 A. interface FastEthernet 0/1
channel-group 1 mode active
switchport trunk encapsulation dot1q
switchport mode trunk
interface FastEthernet 0/2
channel-group 1 mode active
switchport trunk encapsulation dot1q
switchport mode trunk
B. interface FastEthernet 0/1
channel-group 2 mode auto
switchport trunk encapsulation dot1q
switchport mode trunk
interface FastEthernet 0/2
channel-group 2 mode auto
switchport trunk encapsulation dot1q
switchport mode trunk
C. interface FastEthernet 0/1
channel-group 1 mode desirable
switchport trunk encapsulation dot1q
switchport mode trunk
interface FastEthernet 0/2
channel-group 1 mode desirable
switchport trunk encapsulation dot1q
switchport mode trunk
D. interface FastEthernet 0/1
channel-group 1 mode passive
switchport trunk encapsulation dot1q
switchport mode trunk
interface FastEthernet 0/2
channel-group 1 mode passive
switchport trunk encapsulation dot1q
switchport mode trunk Answer: C Cisco Certification 200-125 certificate are those engaged in IT industry's dream. You need to choose the professional training by Lead2pass Cisco 200-125 dumps. Lead2pass will be with you, and to ensure the success wherever you may increase pursuit your career. Let Lead2pass take all your heart, let the dream to reality! 200-125 new questions on Google Drive: https://drive.google.com/open?id=0B3Syig5i8gpDbnNGVlNHTzJjcWc 2 2016 Cisco 200-125 exam dumps (All 545 Q&As) from Lead2pass: http://www.lead2pass.com/200-125.html 3 1 [100% Exam Pass Guaranteed]
|










