[PDF&VCE] Lead2pass 300-115 New Questions Free Download (81-100)
2016 October Cisco Official New Released 300-115 Dumps in Lead2pass.com! 100% Free Download! 100% Pass Guaranteed! There is no need to hassle if you are stuck in the 300-115 exam difficulties, Lead2pass will assist you right through 300-115 exam with 300-115 PDF and VCE dumps. Lead2pass delivers the most comprehensive 300-115 exam preparation material, covering each and every aspect of 300-115 exam curriculum. We ensure you 100% success in 300-115 exam. Following questions and answers are all new published by Cisco Official Exam Center: http://www.lead2pass.com/300-115.html QUESTION 81
Which AAA Authorization type includes PPP, SLIP, and ARAP connections? A. network
B. IP mobile
C. EXEC
D. auth-proxy 
Answer: A QUESTION 82
Which authentication service is needed to configure 802.1x? A. RADIUS with EAP Extension
B. TACACS+
C. RADIUS with CoA
D. RADIUS using VSA Answer: A QUESTION 83
Refer to the exhibit. Which login credentials are required when connecting to the console port in this output?
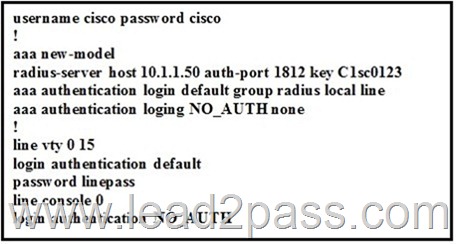 A. none required
B. username cisco with password cisco
C. no username with password linepass
D. login authentication default Answer: A QUESTION 84
Refer to the exhibit. When a network administrator is attempting an SSH connection to the device, in which order does the device check the login credentials?
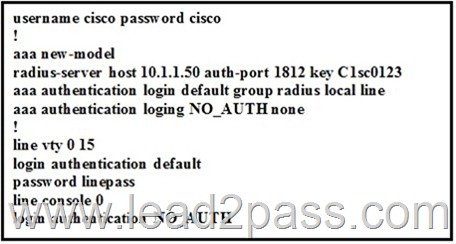 A. RADIUS server, local username, line password
B. RADIUS server, line password, local username
C. Line password, local username, RADIUS server
D. Line password, RADIUS server, local username Answer: A QUESTION 85
Which type of information does the DHCP snooping binding database contain? A. untrusted hosts with leased IP addresses
B. trusted hosts with leased IP addresses
C. untrusted hosts with available IP addresses
D. trusted hosts with available IP addresses Answer: A QUESTION 86
Which switch feature determines validity based on IP-to-MAC address bindings that are stored in a trusted database? A. Dynamic ARP Inspection
B. storm control
C. VTP pruning
D. DHCP snooping Answer: A QUESTION 87
Which command is needed to enable DHCP snooping if a switchport is connected to a DHCP server? A. ip dhcp snooping trust
B. ip dhcp snooping
C. ip dhcp trust
D. ip dhcp snooping information Answer: A QUESTION 88
When you configure private VLANs on a switch, which port type connects the switch to the gateway router? A. promiscuous
B. community
C. isolated
D. trunked Answer: A QUESTION 89
When you configure a private VLAN, which type of port must you configure the gateway router port as? A. promiscuous port
B. isolated port
C. community port
D. access port Answer: A QUESTION 90
Which First Hop Redundancy Protocol is an IEEE Standard? A. GLBP
B. HSRP
C. VRRP
D. OSPF Answer: C QUESTION 91
What is the default amount by which the hot standby priority for the router is decremented or incremented when the interface goes down or comes back up? A. 1
B. 5
C. 10
D. 15 Answer: C QUESTION 92
What is the maximum number of virtual MAC addresses that GLBP allows per group? A. 2
B. 4
C. 6
D. 8 Answer: B QUESTION 93
Which gateway role is responsible for answering ARP requests for the virtual IP address in GLBP? A. active virtual forwarder
B. active virtual router
C. active virtual gateway
D. designated router Answer: C QUESTION 94
Which VRRP router is responsible for forwarding packets that are sent to the IP addresses of the virtual router? A. virtual router master
B. virtual router backup
C. virtual router active
D. virtual router standby Answer: A QUESTION 95
Which command correctly configures standby tracking for group 1 using the default decrement priority value? A. standby 1 track 100
B. standby 1 track 100 decrement 1
C. standby 1 track 100 decrement 5
D. standby 1 track 100 decrement 20 Answer: A QUESTION 96
Which command configures an HSRP group to become a slave of another HSRP group? A. standby slave
B. standby group track
C. standby follow
D. standby group backup Answer: C QUESTION 97
Refer to the exhibit. Which option describes the reason for this message in a GLBP configuration?
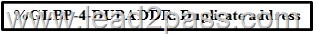 A. Unavailable GLBP active forwarder
B. Incorrect GLBP IP address
C. HSRP configured on same interface as GLBP
D. Layer 2 loop Answer: D QUESTION 98
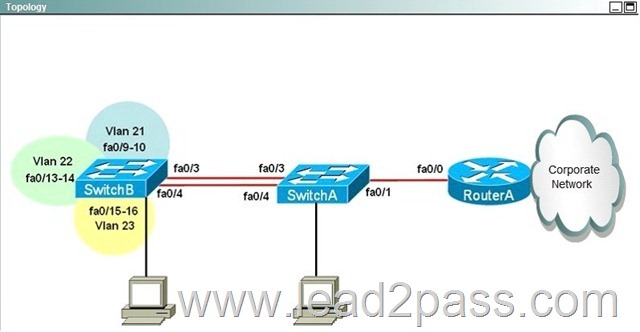
Lab Simulation - LACP with STP Sim
You work for SWITCH.com. They have just added a new switch (SwitchB) to the existing network as shown in the topology diagram.
RouterA is currently configured correctly and is providing the routing function for devices on SwitchA and SwitchB. SwitchA is currently configured correctly, but will need to be modified to support the addition of SwitchB. SwitchB has a minimal configuration. You have been tasked with competing the needed configuring of SwitchA and SwitchB. SwitchA and SwitchB use Cisco as the enable password.
Configuration Requirements for SwitchA
The VTP and STP configuration modes on SwitchA should not be modified.
- SwitchA needs to be the root switch for vlans 11, 12, 13, 21, 22 and 23. All other vlans should be left are their default values.
Configuration Requirements for SwitchB
- Vlan 21
Name: Marketing
will support two servers attached to fa0/9 and fa0/10
- Vlan 22
Name: Sales
will support two servers attached to fa0/13 and fa0/14
- Vlan 23
Name: Engineering
will support two servers attached to fa0/15 and fa0/16
- Access ports that connect to server should transition immediately to forwarding state upon detecting the connection of a device.
- SwitchB VTP mode needs to be the same as SwitchA.
- SwitchB must operate in the same spanning tree mode as SwitchA
- No routing is to be configured on SwitchB
- Only the SVI vlan 1 is to be configured and it is to use address 192.168.1.11/24
Inter-switch Connectivity Configuration Requirements
- For operational and security reasons trunking should be unconditional and Vlans 1, 21, 22 and 23 should tagged when traversing the trunk link.
- The two trunks between SwitchA and SwitchB need to be configured in a mode that allows for the maximum use of their bandwidth for all vlans. This mode should be done with a non-proprietary protocol, with SwitchA controlling activation.
- Propagation of unnecessary broadcasts should be limited using manual pruning on this trunk link.
Answer:
SW-A (close to router)
SW-A#configure terminal
SW-A(config)#spanning-tree vlan 11-13,21-23 root primary
SW-A(config)#vlan 21
SW-A(config-vlan)#name Marketing
SW-A(config-vlan)#exit
SW-A(config)#vlan 22
SW-A(config-vlan)#name Sales
SW-A(config-vlan)#exit
SW-A(config)#vlan 23
SW-A(config-vlan)#name Engineering
SW-A(config-vlan)#exit
SW-A(config)#interface range Fa0/3 – 4
SW-A(config-if-range)#no switchport mode access
SW-A(config-if-range)#no switchport access vlan 98 (These two commands must be deleted to form a trunking link)
SW-A(config-if-range)#switchport trunk encapsulation dot1q (cannot issued this command on this switch, but don‘t worry coz I still got 100%)
SW-A(config-if-range)#switchport mode trunk
SW-A(config-if-range)#switchport trunk native vlan 99
SW-A(config-if-range)#switchport trunk allowed vlan 1,21-23
SW-A(config-if-range)#channel-group 1 mode active
SW-A(config-if-range)#channel-protocol lacp
SW-A(config-if-range)#no shutdown
SW-A(config-if-range)#end SW-B (far from router)
SW-B#configure terminal
SW-B(config)#vlan 21
SW-B(config-vlan)#name Marketing
SW-B(config-vlan)#exit
SW-B(config)#vlan 22
SW-B(config-vlan)#name Sales
SW-B(config-vlan)#exit
SW-B(config)#vlan 23
SW-B(config-vlan)#name Engineering
SW-B(config-vlan)#exit
SW-B(config)#vlan 99
SW-B(config-vlan)#name TrunkNative // not necessary to name it but just name it same as SwitchA
SW-B(config-vlan)#exit
SW-B(config)#interface range Fa0/9 – 10
SW-B(config-if-range)#switchport mode access
SW-B(config-if-range)#switchport access vlan 21
SW-B(config-if-range)#spanning-tree portfast
SW-B(config-if-range)#no shutdown
SW-B(config-if-range)#exit
SW-B(config)#interface range Fa0/13 – 14
SW-B(config-if-range)#switchport mode access
SW-B(config-if-range)#switchport access vlan 22
SW-B(config-if-range)#spanning-tree portfast
SW-B(config-if-range)#no shutdown
SW-B(config-if-range)#exit
SW-B(config)#interface range Fa0/15 – 16
SW-B(config-if-range)#switchport mode access
SW-B(config-if-range)#switchport access vlan 23
SW-B(config-if-range)#spanning-tree portfast
SW-B(config-if-range)#no shutdown
SW-B(config-if-range)#exit
SW-B(config)#vtp mode transparent
SW-B(config)#spanning-tree mode rapid-pvst
SW-B(config)#ip default-gateway 192.168.1.1 (you can get this IP from SW-A with command show cdp neighbour detail) // not sure about this command because the question says “No routing is to be configured on SwitchB”.
SW-B(config)#interface vlan 1
SW-B(config-if)#ip address 192.168.1.11 255.255.255.0
SW-B(config-if)#no shutdown
SW-B(config-if)#exit
SW-B(config)#interface range Fa0/3 – 4
SW-B(config-if-range)#switchport trunk encapsulation dot1q (yes I can issued this command on this switch)
SW-B(config-if-range)#switchport mode trunk
SW-B(config-if-range)#switchport trunk native vlan 99
SW-B(config-if-range)#switchport trunk allowed vlan 1,21-23
SW-B(config-if-range)#channel-group 1 mode passive //mode passive because “SwitchA controlling activation”
SW-B(config-if-range)#channel-protocol lacp
SW-B(config-if-range)#no shutdown
SW-B(config-if-range)#end Some guidelines for configuring SwitchA & SwitchB:
Configuration Requirements for SwitchA
- The VTP and STP configuration modes on SwitchA should not be modified.
– SwitchA needs to be the root switch for vlans 11, 12, 13, 21, 22 and 23. All other vlans should be left are their default values SW-A(config)#spanning-tree vlan 11-13,21-23 root primary
Configuration Requirements for SwitchB
- Vlan 21, Name: Marketing, will support two servers attached to fa0/9 and fa0/10
– Vlan 22, Name: Sales, will support two servers attached to fa0/13 and fa0/14
– Vlan 23, Name: Engineering, will support two servers attached to fa0/15 and fa0/16
– Access ports that connect to server should transition immediately to forwarding state upon detecting the connection of a device. vlan …
name …
(VLANs must be created on both switches if not exist)
interface range Fa0/x – x
switchport mode access
switchport access vlan
spanning-tree portfast
- SwitchB VTP mode needs to be the same as SwitchA. vtp mode transparent
- SwitchB must operate in the same spanning tree mode as SwitchA. spanning-tree mode rapid-pvst
- No routing is to be configured on SwitchB.
– Only the SVI vlan 1 is to be configured and it is to use address 192.168.1.11/24. interface vlan 1
ip address 192.168.1.11 255.255.255.0
Inter-switch Connectivity Configuration Requirements:
- For operational and security reasons trunking should be unconditional and Vlans 1, 21, 22 and 23 should tagged when traversing the trunk link. SW-A(config)#interface range Fa0/3 – 4
SW-A(config-if)#no switchport mode access
SW-A(config-if)#no switchport access vlan 98 //These two commands must be deleted to form a trunking link.
SW-A(config-if)#switchport mode trunk
SW-A(config-if)#switchport trunk native vlan 99
—————————————
SW-B(config)#interface range Fa0/3 – 4
SW-B(config-if)#switchport trunk encapsulation dot1q (yes I can issued this command on this switch)
SW-B(config-if)#switchport mode trunk
SW-B(config-if)#switchport trunk native vlan 99
- The two trunks between SwitchA and SwitchB need to be configured in a mode that allows for the maximum use of their bandwidth for all vlans. This mode should be done with a non-proprietary protocol, with SwitchA controlling activation. SW-A(config)#interface range Fa0/3 – 4
SW-A(config-if)#channel-group 1 mode active
SW-A(config-if)#channel-protocol lacp
SW-A(config-if)#no shutdown
—————————————
SW-B(config)#interface range Fa0/3 – 4
SW-B(config-if)#channel-group 1 mode passive
SW-B(config-if)#channel-protocol lacp
SW-B(config-if)#no shutdown
—————————————
Maybe the interface Port-channel 1 was configured on both switches so we don't configure it here. If not we have to configure them with “interface port-channel 1″ command. Also you have to turn them up.
- Propagation of unnecessary broadcasts should be limited using manual pruning on this trunk link. SW-A(config)#interface range Fa0/3 – 4
SW-A(config-if)#switchport trunk allowed vlan 1,21-23
—————————————
SW-B(config)#interface range Fa0/3 – 4
SW-B(config-if)#switchport trunk allowed vlan 1,21-23 You may have to configure Interface Port-Channel on both switches. Check the configuration first, if it does not exist, use these commands:
interface port-channel1
switchport mode trunk
switchport trunk native vlan 99 //this command will prevent the “Native VLAN mismatched” error on both switches
switchport trunk allowed vlan 1,21-23,99
Some notes for this sim:
+ You should check the initial status of both switches with these commands: show vtp status (transparent mode on switchA and we have to set the same mode on switchB), show spanning-tree [summary] (rapid-pvst mode on switchA and we have to set the same mode on switchB), show vlan (check the native vlan and the existence of vlan99), show etherchannel 1 port-channel and show ip int brief (check if Port-channel 1 has been created and make sure it is up), show run (to check everything again).
+ When using “int range f0/x - y” command hit space bar before and after “-“ otherwise the simulator does not accept it.
+ You must create vlan 99 for the switchB. SwitchA already have vlan 99 configured.
+ At the end, you can try to ping from SwitchB to RouterA (you can get the IP on RouterA via the show cdp neighbors detail on SwitchA), not sure if it can ping or not. If not, you can use the “ip default-gateway 192.168.1.1” on SwitchB.
+ The name of SwitchA and SwitchB can be swapped or changed so be careful to put your configuration into appropriate switch. QUESTION 99
Lab Simulation - AAAdot1x
SWITCH.com is an IT company that has an existing enterprise network comprised of two layer 2 only switches; DSW1 and ASW1. The topology diagram indicates their layer 2 mapping. VLAN 20 is a new VLAN that will be used to provide the shipping personnel access to the server. Corporate polices do not allow layer 3 functionality to be enabled on the switches.
For security reasons, it is necessary to restrict access to VLAN 20 in the following manner:
- Users connecting to VLAN 20 via portfO/1 on ASW1 must be authenticated before they are given access to the network. Authentication is to be done via a Radius server:
- Radius server host: 172.120.40.46
- Radius key: rad123
- Authentication should be implemented as close to the host as possible.
- Devices on VLAN 20 are restricted to the subnet of 172.120.40.0/24.
- Packets from devices in the subnet of 172.120.40.0/24 should be allowed on VLAN 20.
- Packets from devices in any other address range should be dropped on VLAN 20.
- Filtering should be implemented as close to the serverfarm as possible.
The Radius server and application servers will be installed at a future date. You have been tasked with implementing the above access control as a pre-condition to installing the servers. You must use the available IOS switch features.
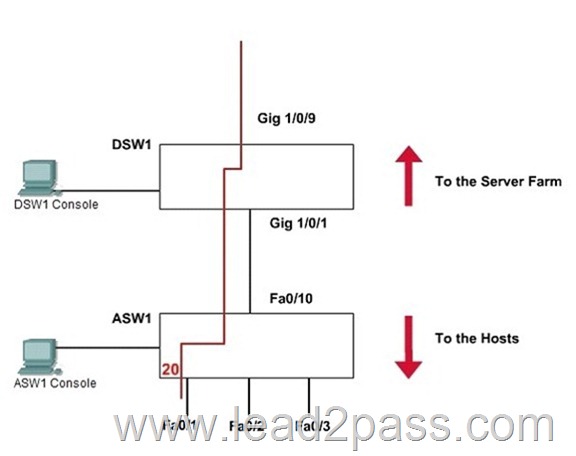
Answer:
1. Verification of Pre-configuration:
a. Check that the denoted vlan [vlan20] is created in both switches and ports [fa0/1 of ASW1] are assigned.
b. Take down the radius-server ip [172.120.39.46] and the key [rad123].
c. Take down the IP range [172.120.40.0/24] to be allowed the given vlan [vlan20]
2. Configure the Port based authentication on ASW1:
Enable AAA on the switch:
ASW1(config)# aaa new-model
The new-model keyword refers to the use of method lists, by which authentication methods and sources can be grouped or organized. Define the server along with its secret shared password:
ASW1(config)# radius-server host 172.120.39.46 key rad123
ASW1(config)# aaa authentication dot1x default group radius
This command causes the RADIUS server defined on the switch to be used for 802.1x authentication.
Enable 802.1x on the switch:
ASW1(config)# dot1x system-auth-control
Configure Fa0/1 to use 802.1x:
ASW1(config)# interface fastEthernet 0/1
ASW1(config-if)# switchport mode access
ASW1(config-if)# dot1x port-control auto
Notice that the word “auto” will force connected PC to authenticate through the 802.1x exchange.
ASW1(config-if)# exit
ASW1# copy running-config startup-config
3. Filter the traffic and create vlan access-map to restrict the traffic only for a range on DSW1
Define an access-list:
DSW1(config)# ip access-list standard 10 (syntax: ip access-list {standard | extended} acl-name)
DSW1(config-ext-nacl)# permit 172.120.40.0 0.0.0.255
DSW1(config-ext-nacl)# exit
Define an access-map which uses the access-list above:
DSW1(config)# vlan access-map MYACCMAP 10 (syntax: vlan access-map map_name [0-65535] )
DSW1(config-access-map)# match ip address 10 (syntax: match ip address {acl_number | acl_name})
DSW1(config-access-map)# action forward
DSW1(config-access-map)# exit
DSW1(config)# vlan access-map MYACCMAP 20
DSW1(config-access-map)# action drop (drop other networks)
DSW1(config-access-map)# exit
Apply a vlan-map into a vlan:
DSW1(config)# vlan filter MYACCMAP vlan-list 20 (syntax: vlan filter mapname vlan-list list)
DSW1# copy running-config startup-config
4. Note:
It is not possible to verify the configuration in this lab. All we have do the correct configurations. Most of the exam takers report that “ copy running-config startup-config” is not working. It does not a matter.
Do not try unwanted/wrong commands in the consoles. They are not real switches. QUESTION 100
Hotspot - HSRP
Ferris Plastics, Inc. is a medium sized company, with an enterprise network (access, distribution and core switches) that provides LAN connectivity from user PCs to corporate servers. The distribution switches are configured to use HSRPto provide a high availability solution.
- DSW1 -primary device for VLAN 101 VLAN 102 andVLAN 105
- DSW2 - primary device for VLAN 103 and VLAN 104
- A failure of GigabitEthemet1/0/1 on primary device should cause the primary device to release its status as the primary device, unless GigabitEthernet1/0/1 on backup device has also failed.
Troubleshooting has identified several issues. Currently all interfaces are up. Using the running configurations and show commands, you have been asked to investigate and respond to the following question.
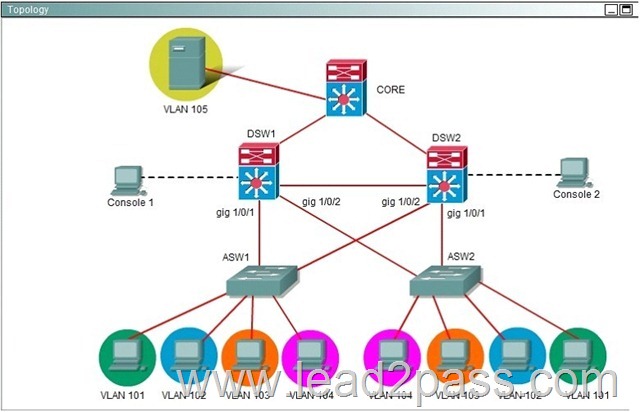
During routine maintenance, GigabitEthernet1/0/1 on DSW1 was shut down. All other interfaces were up. DSW2 became the active HSRP device for VLAN 101 as desired. However, after GigabitEthemet1/0/1 on DSW1 was reactivated, DSW1 did not become the active router for VLAN 101 as desired. What needs to be done to make the group for VLAN 101 function properly? A. Enable preempt in the VLAN 101 HSRP group on DSW1.
B. Disable preempt in the VLAN 101 HSRP group on DSW2's.
C. In the VLAN 101 HSRP group on DSW1, decrease the priority value to avaluethatis less ' than the priority value configured in the VLAN 101 HSRP group on DSW2.
D. Decrease the decrement value in the track command for the VLAN 101 HSRP group on U DSWTs to a values less than the value in the track command for the VLAN 101 HSRP group on DSW2. Answer: A
Explanation:
A is correct. All other answers is incorrect. Because Vlan101 on DS1 ( left ) disable preempt. We need enable preempt to after it reactive, it will be active device. If not this command, it never become active device. We highly recommend our 300-115 dumps. Comparing with others', Lead2pass is the most credible and authentic source of information on 300-115 exam and we strive to keep our 300-115 dumps up-to-date and reliable on a consistent basis. Our exam preparation material is rich in variety. We offer 300-115 PDF format and 300-115 practice test with free VCE player. That's the reason why many candidates choose Lead2pass. 300-115 new questions on Google Drive: https://drive.google.com/open?id=0B3Syig5i8gpDS21vUTdBQVgxWFk 2016 Cisco 300-115 exam dumps (All 230 Q&As) from Lead2pass: http://www.lead2pass.com/300-115.html [100% Exam Pass Guaranteed]
|




