[PDF&VCE] 350-018 Latest Dumps Free Download From Lead2pass (838-858)
2016 November Cisco Official New Released 350-018 Dumps in Lead2pass.com! 100% Free Download! 100% Pass Guaranteed! There is no need to hassle if you are stuck in the 350-018 exam difficulties, Lead2pass will assist you right through 350-018 exam with 350-018 PDF and VCE dumps. Lead2pass delivers the most comprehensive 350-018 exam preparation material, covering each and every aspect of 350-018 exam curriculum. We ensure you 100% success in 350-018 exam. Following questions and answers are all new published by Cisco Official Exam Center: http://www.lead2pass.com/350-018.html QUESTION 838
Why is the IPv6 type 0 routing header vulnerable to attack? A. It allows the sender to generate multiple NDP requests for each packet
B. It allows the receiver of a packet to control its flow
C. It allows the sender to generate multiple ARP requests for each packet
D. it allows the sender of a packet to control its flow.
E. It allows the receiver of a packet to modify the source IP address 
Answer: D QUESTION 839
Which two statements about the send protocol are true?(Choose two) A. it counters neighbor discovery threats
B. it must be enabled before you can configure IPv6 address
C. It supports numerous custom neighbor discovery messages
D. it supports an auto configuration mechanism
E. it logs IPv6-related threats to an external log server
F. it uses IPsec as baseline mechanism Answer: AD QUESTION 840
In a Cisco ASA multiple-context mode of operation configuration ,what three session types are resource-limited by default when their context is a member of the default class?(Choose three) A. ASDM sessions
B. Telnet sessions
C. IPSec sessions
D. SSL VPN sessions
E. TCP sessions F.SSH sessions Answer: AB QUESTION 841
You have discovered an unwanted device with MAC address 001c.of12.badd on port FastEthernet1/1 on VLAN 4.
What command or command sequence can enter on the switch to prevent the MAC address from passing traffic on VLAN 4?
 A. Option A
B. Option B
C. Option C
D. Option D Answer: C QUESTION 842
Refer to exhibit. What is the effect to the given configuration? 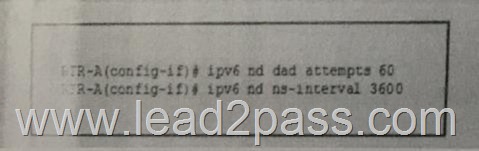
A. It sets the duplicated address detection Interval to 60 seconds and sets the IPv6 Neighbor solicitation Interval to 3600 milliseconds.
B. It sets the number of neighbor solicitation messages to 60 while duplicate address detection is performed and sets the neighbor solicitation retransmission interval to 3600 milliseconds.
C. It sets the number of neighbor solicitation messages to 60 and sets the duplicate address detection interval to 3600 seconds.
D. It sets dulicate address detection interval to 60 seconds and sets the IPv6 neighbor reachable time to 3600 milliseconds.
E. It sets the number of duplicate address detection attempts to 60 and sets the duplicate address detection interval to 3600 milliseconds. Answer: B QUESTION 843
Refer to the exhibit. What is the meaning of the given error message?
 A. The PFS groups are mismatched
B. IKES disabled on the remote peer
C. The pre-shared keys are mismatched
D. The mirrored crypto ACLs are mismatched Answer: C QUESTION 844
You are developing an application to manage the traffic flow of a switch using an OpenDaylight controller.
Knowing you use a Northbound which statement is true? A. We must teach our applications about the Southbound protocol(s) used.
B. Different applications, even in different languages, cannot use the same functions in a REST API at the same time.
C. The applications are considered to be the clients, and the controller is considered to be the server
D. The server retains client state records Answer: C QUESTION 845
Which two statements about IKEv2 are true?(Choose two) A. it uses EAP authentication at minimum.
B. A complete proposal requires one encryption algorithm and one integrity algorithm.
C. The profile contains a repository of symmetric and asymmetric and asymmetric preshared keys.
D. It uses X.509 certificates for authentication
E. The profile is a collection of transforms used to negotiate IKE SAS
F. It supports DPD and NAT-T by default. Answer: AF QUESTION 846
Which object table contains informations about the clients know to the server in Cisco NHRP MIB implementation? A. NHRP Server NHC Table
B. NHRP Client Statistics Table
C. NHRP Cache Table
D. NHRP Purge Request Table Answer: A QUESTION 847
Your IPv6 a CA and trust anchous to implement secure network discovery.
What extension must your CA certificates support? A. id-pe-ipaddrBlocks
B. keyUsage
C. extKeyUsage
D. id-pe-autonomousSyslds
E. nameConstraints Answer: E QUESTION 848
A cloud service provider is designing a large mulitienant data center to support thousands of tensants. The provider is concerned about the scalability the layer 2 network and providing layer 2 segmentation to potentially thousands of tenants.
Which layer 2 technology is best suited in this scenario? A. extended VLAN ranges
B. VXLAN
C. VRF
D. LDP Answer: B QUESTION 849
Which two statements about the IPv6 Hop-by-Hop Options extension header (EH) are true?(Choose two) A. The Hop-by-Hop EH is processed in hardware by all intermediate network devices
B. The Hop-by-Hop extension header is processed by the CPU by network devices
C. The Hop-by-Hop EH is encrypted by the Encapsulating Security Header
D. If present, the Hop-by-Hop EH must fllow the Mobility EH.
E. If present, network devices must process the Hop-by-Hop EH first
F. The Hop-by-Hop EH is processed in hardware at the source and the destination devices only Answer: BE QUESTION 850
CCMP(CCM mode Protocol) is based on which algorithm? A. AES
B. RCS
C. 3DES
D. IDEA
E. Blowfish Answer: A QUESTION 851
Refer to the exhibit. R1 and R2 are failing to establish a BGP neighbor relationship.
What is a Possible reason for the problem?
 A. The neighbor remote-as command on R2 uses an incorrect AS number
B. The BGP timers on R1 and R2 are different
C. R2 is configured with a private AS
D. The no synchronization command is missing from R1'S configuration
E. The dbgp-multihop values on R1 and R2 are different
F. The no auto-summary command is missing from R2'S configuration. Answer: A QUESTION 852
If a cisco ASA firewall that is configured in multiple-context mode of operation receives a packet whose destination MAC address is a multicast address, how is the packet routed? A. The Packets dropped
B. The packet is duplicated and forwarded to every context
C. The packet is forwarded to the admin context only
D. The packet duplicated and forwarded to every context except admin Answer: B QUESTION 853
Refer to the exhibit. Which statement about this configuration is true?
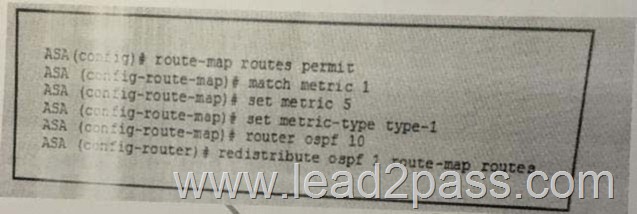 A. The ASA injects a static default route into OSPF process 1
B. The ASA injects a static default route into OSPF process 1
C. The ASF stops LSA type 7 packets from flooding into OSPF area 1
D. The ASA redistributes routes from one routing protocol to another
E. The ASA injects a static default route into OSPF area 1
F. The ASA redistributes routes from one OSPF process to another Answer: F QUESTION 854
You want to enable users in your company's branch offices to deploy their own access points using WAN links from the central office. But you are un able to deploy a controller in the branch offices. What Lighweight Access Point wireless mode should you choose? A. Local mode
B. Monitor mode
C. REAP mode
D. H-REAP mode
E. TLS mode Answer: D QUESTION 855
You want to network hardware (which IS not part of the ACI Infrastructure) to be governed by the APIC, by Installing device packages.
Where must these package be Installed? A. on all devices on the path
B. on the connecting leaf switches
C. on the network element you are adding
D. on the APIC Answer: D QUESTION 856
Which two options are benefits of Shortcut Switching Enhancements for NHRP on DMVPN networks?(Choose two) A. It supports layered network topologies with central hubs and direct spoke-to-spoke tunnels between spokes on different hubs
B. It allows data packets to be fast switched while spoke-to-spoke tunnels are being established
C. It enables spokes to use a summary route to build spoke-to-spoke tunnels.
D. It enables the NHRP FIB lookup process to perform route summarization on the hub Answer: AC QUESTION 857
Which technology builds on the vPath concept and can be used in virtual and physical environments? A. NSH
B. VXLAN
C. ACL
D. SDN Answer: A QUESTION 858
Refer to the exhibit. Host 1 is assigned the static IP address 10.1.1.200 as shown. But host 2 and host 3 have dynamic IP address. DHCP snooping and dynamic ARP inspection are configure on the network. What command or command sequence must you configure on the network.
What command or command sequence must you configure on the switch to allow Host 1 to communicate with the other hosts?
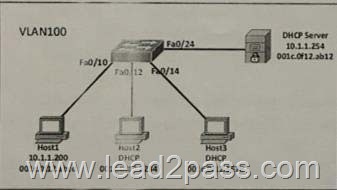 A. Switch(config)#ip source binding 001c.0f12.abcd vlan 100 10.1.1.200 interface f0/10
B. Switch(config)#interface f0/10 Switch(config-if)#ip dhcp snooping trust
C. Switch(config)#no arp inspection enable
D. Switch(config)#ip dhcp relay information option
E. Switch(config)#arp 10.1.1.200 001c.0f12.abcd arpa
F. Switch(config)# interface f0/10 Switch(config-if)#switchport access vlan 100 Switch(config-if)#switchport mode host Answer: A We highly recommend our 350-018 dumps. Comparing with others', Lead2pass is the most credible and authentic source of information on 350-018 exam and we strive to keep our 350-018 dumps up-to-date and reliable on a consistent basis. Our exam preparation material is rich in variety. We offer 350-018 PDF format and 350-018 practice test with free VCE player. That's the reason why many candidates choose Lead2pass. 350-018 new questions on Google Drive: https://drive.google.com/open?id=0B3Syig5i8gpDU2RpRGdWY3E1NEU 2016 Cisco 350-018 exam dumps (All 894 Q&As) from Lead2pass: http://www.lead2pass.com/350-018.html [100% Exam Pass Guaranteed]
|





