[Full Version] Free Lead2pass Cisco 300-320 VCE And PDF Instant Download (201-220)
2016 December Cisco Official New Released 300-320 Dumps in Lead2pass.com! 100% Free Download! 100% Pass Guaranteed! Lead2pass presents the highest quality of 300-320 exam question which helps candidates to pass the 300-320 exams in the first attempt. Lead2pass professional tools like questions and answers are extremely reliable source of preparation. When you use Lead2pass preparation products your success in the Certification exam is guaranteed.
Following questions and answers are all new published by Cisco Official Exam Center: http://www.lead2pass.com/300-320.html QUESTION 201
Drag and Drop Question 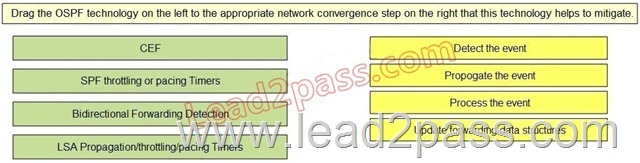
Answer: 
QUESTION 202
Which of these Layer 2 access designs does not support VLAN extensions?
A. FlexLinks
B. loop-free U
C. looped square
D. looped triangle
E. loop-free inverted U Answer: B
QUESTION 203
Which statement about Fibre Channel communications is correct?
A. N_Port to N_Port connections use logical node connection points.
B. Flow control is only provided by QoS.
C. It must be implemented in an arbitrated loop.
D. Communication methods are similar to those of an Ethernet bus. Answer: A
QUESTION 204
In base e-Commerce module designs, where should firewall perimeters be placed?
A. core layer
B. Internet boundary
C. aggregation layer
D. aggregation and core layers
E. access and aggregation layers Answer: A
QUESTION 205
The Cisco Nexus 1000V is intended to address which disadvantage of the VMware vSphere solution?
A. Inability to deploy new functional servers without requiring physical changes on the network
B. Complexity added by the requirement for an ESX host for each virtual machine
C. Network administrators lack control of the access layer of the network
D. To increase the number of physical infrastructure and the virtual machines that can be managed Answer: C
QUESTION 206
With respect to address summarization, which of the following statements concerning IPv4 and IPv6 is true?
A. The potential size of the IPv6 address blocks suggests that address summarization favors IPv6 over IPv4.
B. Role based addressing using wildcard masks to match multiple subnets is suitable for IPv4, but unsuitable for IPv6.
C. In order to summarize, the number of subnets in the IPv4 address block should be a power of 2 while the number of subnets in the IPv6 address block should be a power of 64.
D. WAN link addressing best supports summarization with a /126 subnet for IPv4 and a /31 for IPv6. Answer: B
QUESTION 207
There are 3 steps to confirm whether a range of IP addresses can be summarized. Which of the
following is used in each of these 3 steps?
A. The first number in the contiguous block of addresses
B. The last number in the contiguous block of addresses
C. The size of the contiguous block of addresses
D. The subnet mask of the original network address Answer: C
QUESTION 208
A well-designed IP addressing scheme supporting role-based functions within the subnet will result in the most efficient use of which technology?
A. Layer 3 switching in the core
B. Network Admission Control (NAC)
C. IP telephony (voice and video) services
D. ACLs Answer: D
QUESTION 209
Which of the following is true regarding the effect of EIGRP queries on the network design?
A. EIGRP queries will be the most significant issue with respect to stability and convergence
B. EIGRP queries are not a consideration as long as EIGRP has a feasible successor with a next hop AD that is greater than the FD of the current successor route
C. EIGRP queries will only increase the convergence time when there are no EIGRP stubs designed in the network Answer: A
QUESTION 210
Which of the following is a result when designing multiple EIGRP autonomous systems within the Enterprise Campus network?
A. Improves scalability by dividing the network using summary routes at AS boundaries
B. Decreases complexity since EIGRP redistribution is automatically handled in the background
C. Reduces the volume of EIGRP queries by limiting them to one EIGRP AS
D. Scaling is improved when a unique AS is run at the Access, Distribution, and Core layers of the network Answer: A
QUESTION 211
When designing the routing for an Enterprise Campus network it is important to keep which of the following route filtering aspects in mind?
A. Filtering is only useful when combined with route summarization
B. It is best to filter (allow) the default and summary prefixes only in the Enterprise Edge to remote sites or site-to-site IPsec VPN networks
C. IGPs (for example EIGRP or OSPF) are superior to route filtering in avoiding inappropriate transit traffic through remote nodes or inaccurate or inappropriate routing updates
D. The primary limitation of router filtering is that it can only be applied on outbound updates Answer: B
QUESTION 212
Which statement is the most accurate regarding IPsec VPN design for an Enterprise Campus environment?
A. VPN device IP addressing must align with the existing Campus addressing scheme.
B. The choice of a hub-and-spoke or meshed topology ultimately depends on the number of remotes.
C. Sizing and selection of the IPsec VPN headend devices is most affected by the throughput bandwidth requirements for the remote offices and home worker
D. Scaling considerations such as headend configuration, routing protocol choice, and topology have the broadest impact on the design. Answer: D
QUESTION 213
Refer to the exhibit. The Cisco Nexus 1000V in the VMware vSphere solution effectively creates an additional access layer in the virtualized data center network; which of the following 1000V characteristics can the designer take advantage of?
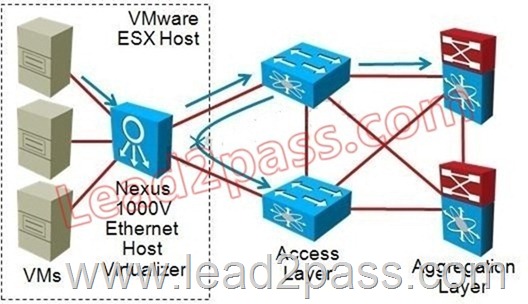
A. Offloads the STP requirement from the external Access layer switches
B. If upstream access switches do not support vPC or VSS the dual-homed ESX host traffic can still be distributed using virtual port channel host mode using subgroups automatically discovered through CDP
C. Allows transit traffic to be forwarded through the ESX host between VMNICs
D. Can be divided into multiple virtual device contexts for service integration, enhanced security, administrative boundaries, and flexibility of deployment Answer: B
QUESTION 214
Which unique characteristics of the Data Center Aggregation layer must be considered by an Enterprise Campus designer?
A. Layer 3 routing between the Access and Aggregation layers facilitates the ability to span VLANs across multiple access switches, which is a requirement for many server virtualization and clustering technologies.
B. "East-west" server-to-server traffic can travel between aggregation modules by way of the core, but backup and replication traffic typically remains within an aggregation module.
C. Load balancing, firewall services, and other network services are commonly integrated by the use of service modules that are inserted in the aggregation switches.
D. Virtualization tools allow a cost effective approach for redundancy in the network design by using two or four VDCs from the same physical switch. Answer: C
QUESTION 215
Support of vPC on the Cisco Nexus 5000 access switch enables various new design options for the data center Access layer, including which of the following?
A. The vPC peer link is not required for Access layer control traffic, and can instead be used to span VLANs across the vPC access switches
B. A single switch can associate per-interface with more than one vPC domain
C. vPC can be used on both sides of the MEC, allowing a unique 16-link EtherChannel to be built between the access and aggregation switches
D. Allows an EtherChannel between a server and a access switch while still maintaining the level of availability that is associated with dual-homing a server to two different access switches Answer: C
QUESTION 216
Which technology is an example of the need for a designer to clearly define features and desired performance when designing advanced WAN services with a service provider?
A. FHRP to remote branches
B. Layer 3 MPLS VPNs secure routing
C. Control protocols (for example Spanning Tree Protocol) for a Layer 3 MPLS service
D. Intrusion prevention, QoS, and stateful firewall support network wide Answer: B
QUESTION 217
Which of the following is true concerning best design practices at the switched Access layer of the traditional layer2 Enterprise Campus Network?
A. Cisco NSF with SSO and redundant supervisors has the most impact on the campus in the Access layer
B. Provide host-level redundancy by connecting each end device to 2 separate Access switches
C. Offer default gateway redundancy by using dual connections from Access switches to redundant
Distribution layer switches using a FHRP
D. Include a link between two Access switches to support summarization of routing information from
the Access to the Distribution layer Answer: A
QUESTION 218
Which protocol will not adhere to the design requirement of the control plane being either separated or combined within a virtualization technology?
A. FHRP
B. STP
C. CEF
D. NSF with SSO Answer: B
QUESTION 219
Which of the following features might be used by the Enterprise Campus network designer as a means of route filtering?
A. IPv4 static routes
B. Route tagging using a route map in an ACL
C. Tagging routes using the BGP MED
D. EIGRP stub networks Answer: D
QUESTION 220
The network designer needs to consider the number of multicast applications and sources in the
network to provide the most robust network possible. Which of the following is a consideration the designer must also address?
A. The IGPs should utilize authentication to avoid being the most vulnerable component
B. With SSM source or receiver attacks are not possible
C. With Shared Trees access control is always applied at the RP
D. Limit the rate of Register messages to the RP to prevent specific hosts from being attacked on a
PIM-SM network Answer: B
Lead2pass is now here to help you with your 300-320 exam certification problems. Because we are the best 300-320 exam questions training material providing vendor, all of our candidates get through 300-320 exam without any problem.
300-320 new questions on Google Drive: https://drive.google.com/open?id=0B3Syig5i8gpDdnA2R2ZwUDFuY2M 2016 Cisco 300-320 exam dumps (All 356 Q&As) from Lead2pass: http://www.lead2pass.com/300-320.html [100% Exam Pass Guaranteed]
|


