[Full Version] 100% Pass Lead2pass 400-251 New Questions Free Version (201-220)
2017 February Cisco Official New Released 400-251 Dumps in Lead2pass.com! 100% Free Download! 100% Pass Guaranteed! Good news, Lead2pass has updated the 400-251 exam dumps. With all the questions and answers in your hands, you will pass the Cisco 400-251 exam easily. Following questions and answers are all new published by Cisco Official Exam Center: http://www.lead2pass.com/400-251.html 3 1 QUESTION 201
Which two statements about DTLS are true?(Choose two) A. It uses two simultaneous IPSec tunnels to carry traffic.
B. If DPD is enabled, DTLS can fall back to a TLS connection.
C. Because it requires two tunnels, it may experience more latency issues than SSL connections.
D. If DTLS is disabled on an interface, then SSL VPN connections must use SSL/TLS tunnels.
E. It is disabled by default if you enable SSL VPN on the interface. 
Answer: BC QUESTION 202
Refer to the exhibit, which two Statements about the given Configuration are true? (Choose two) 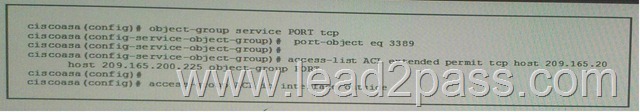
A. It is an inbound policy.
B. It will allow 209.165.202.129 to connect to 202.165.200.225 on an IMAP port.
C. It will allow 209.165.202.129 to connect to 202.165.200.225 on an RDP port.
D. It will allow 202.165.200.225 to connect to 209.165.202.129 on an RDP port.
E. It will allow 202.165.200.225 to connect to 209.165.202.129 on a VNC port.
F. It is an outbound policy. Answer: AC QUESTION 203
What command can you use to protect a router from TCP SYN-flooding attacks? A. ip igmp snooping
B. rate-limit input <bps><burst-normal><Burst-max>
C. ip tcp intercept list <access-list>
D. ip dns spoofing <ip-address>
E. police <bps> Answer: C QUESTION 204
Refer to the exhibit, what is the effect of the given configuration? 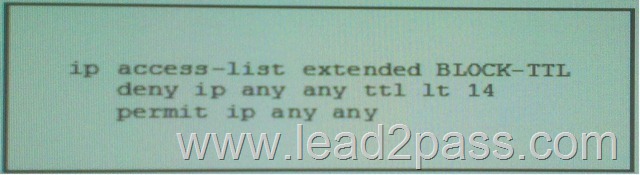
A. It will Drop all TTL packet with a value of 14 in the IP header field.
B. It will Drop all TTL packet with a TTL value less than 14.
C. It will Drop all TTL packet with a TTL value of 15 or more.
D. It will Drop all TTL packet with a TTL value of 14 or more. Answer: B QUESTION 205
If the ASA interfaces on a device are configured in passive mode, which mode must be configured on the remote device to enable EtherChannel? A. standby
B. active
C. on
D. passive Answer: B QUESTION 206
Which three statements about the SHA-2 algorithm are true? (Choose three) A. It provides a variable-length output using a collision-resistant cryptographic hash.
B. It provides a fixed-length output using a collision-resistant cryptographic hash.
C. It is used for integrity verification.
D. It generates a 160-bit message digest.
E. It is the collective term for the SHA-224, SHA-256, SHA-384, and SHA-512 algorithms.
F. It generates a 512-bit message digest. Answer: BCE QUESTION 207
Drag and Drop Question
Drag and drop each RADIUS packet field on the left onto the matching decription on the right. 
Answer: 
QUESTION 208
Which three of these situation warrant engagement of a security incident Response team?(Choose three) A. damage to computer/network resources
B. pornographic biogs'websites
C. computer or network misuse/abuse
D. denial of service (DoS)
E. loss of data confidentialitymtegrity Answer: CDE QUESTION 209
What are three protocol that support layer 7 class maps and policy maps for zone based firewalls? (choose three) A. IMAP
B. RDP
C. MME
D. ICQ
E. POP3
F. IKE Answer: ADE QUESTION 210
You have configured an authenticator switch in access mode on a network configured with NEAT what radius attribute must the ISE server return to change the switch's port mode to trunk? A. device-traffic-class=switch
B. device-traffic-class=trunk
C. framed-protocol=1
D. EAP-message-switch
E. Authenticate=Administrative
F. Acct-Authentic=radius Answer: A QUESTION 211
Refer to the exhibit. Which statement about the router R1 is true? 
A. Its private-config is corrupt.
B. Its NVRAM contains public and private crypto keys.
C. Its running configuration is missing.
D. RMON is configured. Answer: B QUESTION 212
Refer to the Exhibit. What is the effect of the given ACL policy ? 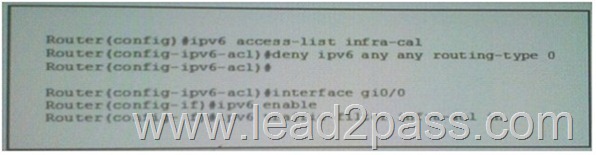
A. The policy will deny all IPv6 eBGP session.
B. The policy will disable IPv6 source routing.
C. The policy will deny all IPv6 routing packet.
D. The policy will deny all IPv6 routed packet. Answer: B QUESTION 213
Which three statements about the RSA algorithm are true? (Choose three.) A. The RSA algorithm provides encryption but not authentication.
B. The RSA algorithm provides authentication but not encryption.
C. The RSA algorithm creates a pair of public-private keys that are shared by entities that perform encryption.
D. The private key is never sent across after it is generated.
E. The public key is used to decrypt the message that was encrypted by the private key.
F. The private key is used to decrypt the message that was encrypted by the public key. Answer: CDF QUESTION 214
Which of these is a core function of the risk assessment process? (Choose one.) A. performing regular network upgrades
B. performing network optimization
C. performing network posture validation
D. establishing network baselines
E. prioritizing network roll-outs Answer: C QUESTION 215
Which two router configurations block packets with the Type 0 Routing header on the interface? (Choose two) A. Ipv6 access-list Deny_Loose_Routing
permit ipv6 any any routing-type 0
deny ipv6 any any
interface FastEthernet0/0
ipv6 traffic-filter Deny_Loose_Source_Routing in
B. Ipv6 access-list-Deny_Loose_Source_Routing
Deny ipv6 FE80::/10 any mobility -type bind-refresh
Interface FastEthernet/0
Ipv6 tr
Affic-filter Deny_Loose_Source_Routing in
C. Ipv6 access-list Deny_Loose_Source_Routing
Deny ipv6 any any routing-type 0
Permit ipv6 any any
Interface FastEthernet0/0
Ipv6 traffic -filter Deny_Loose_Routing in
D. Ipv6 access -list Deny_Loose_Source_Routing
Deny ipv6 any FE80: :/10 routing -type 0
Deny ipv6 any any routing -type 0
Permit ipv6 any any
Interface FastEthernet t0/0
Ipv6 traffic -filter Deny_Loose_Source_Routing in
E. Ipv6 access -list Deny_Loose_Source_Routing
Sequence 1 deny ipv6 any any routing -type 0 log-input
Sequence 2 permit ipv6 any any flow -label 0 routing interface Fastethernet0/0
Ipv6 traffic-filter Deny_Loose_Source_Routing in Answer: CD QUESTION 216
What protocol provides security for datagram protocols? A. MAB
B. DTLS
C. SCEP
D. GET
E. LDP Answer: B QUESTION 217
Which two options are open-source SDN controllers? (Choose two) A. OpenContrail
B. OpenDaylight
C. Big Cloud Fabric
D. Virtual Application Networks SDN Controller
E. Application Policy Infrastructure Controller Answer: AB QUESTION 218
Which current RFC made RFCs 2409, 2407, and 2408 obsolete? A. RFC 4306
B. RFC 2401
C. RFC 5996
D. RFC 4301
E. RFC 1825 Answer: A QUESTION 219
Refer to the exhibit. Which effect of this configuration is true? 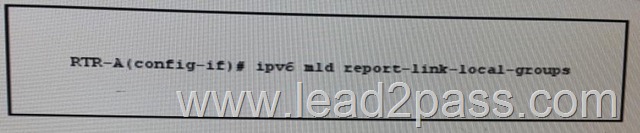
A. It enables MLD query messages for all link-local groups.
B. It configures the node to generate a link-local group report when it joins the solicited- node multicast group.
C. It enables hosts to send MLD report messages for groups 224.0.0.0/24.
D. it enables local group membership for MLDv1 and MLDv2.
E. It enables the host to send MLD report messages for nonlink local groups. Answer: C QUESTION 220
Which technology builds on the vPathconcept and can be used in virtual and physical environments? A. VXLAN
B. ACI
C. NSH
D. SDN Answer: C Once there are some changes on 400-251 exam questions, we will update the study materials timely to make sure that our customer can download the latest edition. 400-251 new questions on Google Drive: https://drive.google.com/open?id=0B3Syig5i8gpDbkNSWnpMam9TWWM 2 2017 Cisco 400-251 exam dumps (All 336 Q&As) from Lead2pass: http://www.lead2pass.com/400-251.html 3 1 [100% Exam Pass Guaranteed]
|






