[Full Version] 100% Pass 400-251 Exam By Training Lead2pass New VCE And PDF Dumps (261-280)
2017 February Cisco Official New Released 400-251 Dumps in Lead2pass.com! 100% Free Download! 100% Pass Guaranteed! Lead2pass is constantly updating 400-251 exam dumps. We will provide our customers with the latest and the most accurate exam questions and answers that cover a comprehensive knowledge point, which will help you easily prepare for 400-251 exam and successfully pass your exam. You just need to spend 20-30 hours on studying the exam dumps. Following questions and answers are all new published by Cisco Official Exam Center: http://www.lead2pass.com/400-251.html 3 1 QUESTION 261
What ASA feature can do use to restrict a user to a specific VPN group? A. A webtypeACL
B. MPF
C. A VPN filter
D. Group-lock 
Answer: D QUESTION 262
Which two statements about SGT Exchange Protocol are true? (Choose two) A. It propagates the IP-to-SGT binding table across network devices that do not have the ability to perform SGT tagging at Layer 2 to devices that support it
B. SXP runs on UDP port 64999
C. A connection is established between a "listener" and a "speaker"
D. SXP is only supported across two hops
E. SXPv2 introduces connection security via TLS Answer: AC QUESTION 263
Which three statements are true regarding RFC 5176 (Change of Authorization)? (Choose three.) A. It defines a mechanism to allow a RADIUS server to initiate a communication inbound to a NAD.
B. It defines a wide variety of authorization actions, including "reauthenticate."
C. It defines the format for a Change of Authorization packet.
D. It defines a DM.
E. It specifies that TCP port 3799 be used for transport of Change of Authorization packets. Answer: ACD QUESTION 264
How does a wireless association flood attack create a DoS? A. It sends a high-power RF pulse that can damage the internals of the AP
B. It spoofs disassociation frames from the access point.
C. It uses a brute force attack to crack the encryption.
D. It exhausts the access client association table. Answer: D QUESTION 265
Refer to the exhibit, you have configured two route-map instances on R1 which passes traffic from switch 1 on both VLAN 1 and VLAN 2.
You wish to ensure that the first route-map instance matches packets from VLAN 1 and sets next hop to 3232::2/128.
The second route-map instance matches packets from VLAN 2 and sets the next hop to 3232::3/128.
What feature can you implement on R1 to make this configuration possible? 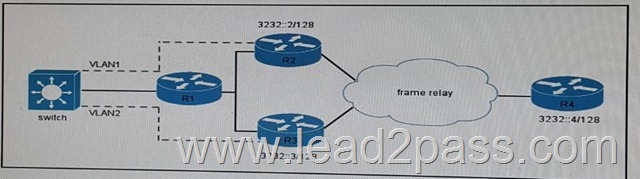
A. PBR
B. BGP local-preference
C. BGP next-hop
D. VSSP
E. GLBP Answer: C QUESTION 266
What are two feature that can be used to drop incoming traffic with spoofed bogon address? (Choose two) A. Unicast RPF
B. ingress ACLs
C. flexible ACLs
D. egress ACLs
E. reflexive ACLs
F. Source Specific Multicast Answer: AB QUESTION 267
Refer to the exhibit, what is the effect of the given command sequence? 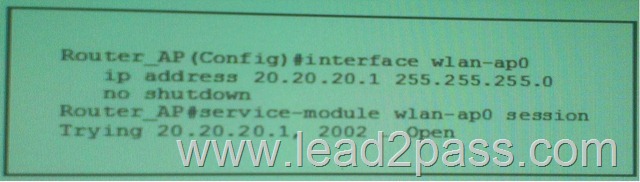
A. The router telnet to the on port 2002
B. The AP console port is shut down.
C. A session is opened between the router console and the AP.
D. The router telnet to the router on port 2002. Answer: QUESTION 268
Which two statements about IPsec in a NAT-enabled environment are true? (Choose two) A. The hashes of each peer's IP address and port number are compared to determine whether NAT-T is required
B. NAT-T is not supported when IPsec Phase 1 is set to Aggressive Mode
C. The first two messages of IPsec Phase 2 are used to determine whether the remote host supports NAT-T
D. NAT-T is not supported when IPsec Phase 1 is set to Main Mode
E. IPsec packets are encapsulated in UDP 500 or UDP 10000 packets
F. To prevent translations from expiring, NAT keepalive messages that include a payload are sent between the peers Answer: AD QUESTION 269
Which statement about the Cisco Secure ACS Solution Engine TACACS+ AV pair is true? A. AV pairs are only required to be enabled on Cisco Secure ACS for successful implementation.
B. The Cisco Secure ACS Solution Engine does not support accounting AV pairs.
C. AV pairs are only string values.
D. AV pairs are of two types: string and integer. Answer: C QUESTION 270
Which statement about Sarbanes-Oxley (SOX) is true? A. SOX is an IEFT compliance procedure for computer systems security.
B. SOX is a US law.
C. SOX is an IEEE compliance procedure for IT management to produce audit reports.
D. SOX is a private organization that provides best practices for financial institution computer systems.
E. Section 404 of SOX is only related to IT compliance. Answer: BE QUESTION 271
Which Cisco ASA firewall mode supports ASDM one-time-password authentication using RSA SecurID? A. Network translation mode
B. Single-context routed mode
C. Multiple-context mode
D. Transparent mode Answer: B QUESTION 272
What protocol is responsible for issuing certificates? A. SCEP
B. DTLS
C. ESP
D. AH
E. GET Answer: A QUESTION 273
Which category to protocol mapping for NBAR is correct? A. Category: internet
Protocol: FTP, HTTP, TFTP
B. Category: Network management
Protocol: ICMP, SNMP, SSH, telent
C. Category: network mail services
Protocol: mapi, pop3, smtp
D. Category: Enterprise applications
Protocal: citrixICA, PCAnywhere, SAP, IMAP Answer: A QUESTION 274
You have discovered unwanted device with MAC address 001c.0f12.badd on port FastEthernet1/1 on VLAN 4.
What command or command sequence can you enter on the switch to prevent the MAC address from passing traffic on VLAN 4? A.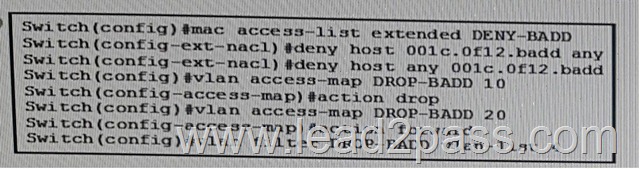
B.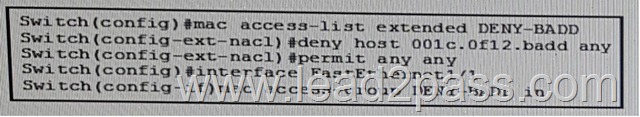
C.
D.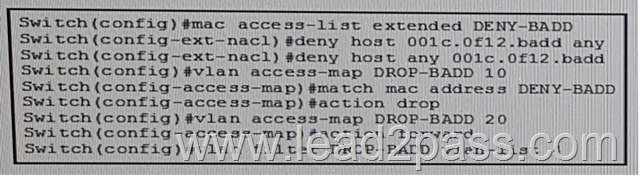
E. Answer: D QUESTION 275
Which two options are benefits of the Cisco ASA Identity Firewall? (Choose two) A. It can apply security policies on an individual user or user-group basis
B. It can identify threats quickly based on their URLs
C. It can operate completely independently of other services
D. It decouples security policies from the network topology
E. It supports an AD server module to verify identity data Answer: AD QUESTION 276
Refer to the exhibit. Which effect of this command is true? 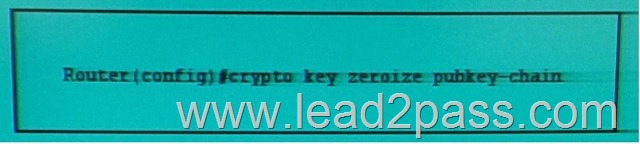
A. The current public key of the router is deleted from the cache when the router reboots, and the router generates a new one.
B. The CA revokes the public key certificate of the router.
C. The public key of the remote peer is deleted from the router cache.
D. The router immediately deletes its current public key from the cache and generates a new one.
E. The router sends a request to the CA to delete the router certificate from its configuration. Answer: C QUESTION 277
Refer to the exhibit. If you apply the given command to a Cisco device running IOS or IOS XE, which two statements about connections to the HTTP server on the device are true?(Choose two) 
A. The device will close each connection after 90 seconds even if a connection is actively processing a request.
B. Connections will close after 60 seconds without activity or 90 seconds with activity.
C. Connections will close after 60 seconds or as soon as the first request is processed.
D. When you apply the command , the device will immediately close any existing connections that have been open for longer than 90 seconds.
E. Connections will close after 60 seconds without activity or as soon as the first request is processed. Answer: CE QUESTION 278
Which two statements about global ACLs are true? (Choose two) A. They support an implicit deny
B. They are applied globally instead of being replicated on each interface
C. They override individual interface access rules
D. They require an explicit deny
E. They can filer different packet types than extended ACLs
F. They require class-map configuration Answer: AB QUESTION 279
What are two security controls you can implement to protect your organization's network from virus and worm outbreak? (Choose two) A. Require users to authenticate before accessing the network
B. Quarantine hosts that fail to meet your organization's IT security requirements
C. Implement Cisco identity service Engine (ISE. for network security
D. Implement routing protocols with strong interface authentication
E. Deploy Cisco prime LMS to manage network security Answer: BC QUESTION 280
Which two statement about DHCP snooping are true? (Choose two) A. The binding database stores information about trusted interface.
B. Massages sent from outside the service-provider network are untrusted.
C. The binding database stores information about both IP and MAC addresses.
D. The lease time in the binding database is a pre-set value.
E. DHCP servers connect to untrusted interface on the switch. Answer: CD Lead2pass is no doubt your best choice. Using the Cisco 400-251 exam dumps can let you improve the efficiency of your studying so that it can help you save much more time. 400-251 new questions on Google Drive: https://drive.google.com/open?id=0B3Syig5i8gpDbkNSWnpMam9TWWM 2 2017 Cisco 400-251 exam dumps (All 336 Q&As) from Lead2pass: http://www.lead2pass.com/400-251.html 3 1 [100% Exam Pass Guaranteed]
|








