[Full Version] 100% Pass 400-251 Exam By Training Lead2pass New VCE And PDF Dumps (21-40)
2017 February Cisco Official New Released 400-251 Dumps in Lead2pass.com! 100% Free Download! 100% Pass Guaranteed! 400-251 dumps free share: Lead2pass presents the highest quality of 400-251 exam dump which helps candidates to pass the 400-251 exams in the first attempt. Following questions and answers are all new published by Cisco Official Exam Center: http://www.lead2pass.com/400-251.html QUESTION 21 Refer to the exhibit which two statement about the given IPV6 ZBF configuration are true? (Choose two) 
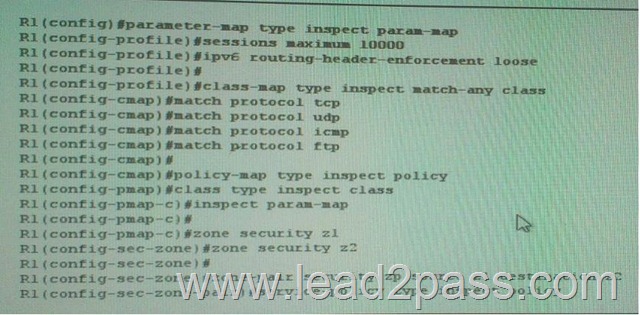
A. It provides backward compability with legacy IPv6 inspection
B. It inspect TCP, UDP,ICMP and FTP traffic from Z1 to Z2.
C. It inspect TCP, UDP,ICMP and FTP traffic from Z2 to Z1.
D. It inspect TCP,UDP,ICMP and FTP traffic in both direction between z1 and z2.
E. It passes TCP, UDP,ICMP and FTP traffic from z1 to z2.
F. It provide backward compatibility with legacy IPv4 inseption. Answer: AB QUESTION 22
In which class of applications security threads does HTTP header manipulation reside? A. Session management
B. Parameter manipulation
C. Software tampering
D. Exception managements Answer: A QUESTION 23
What is the most commonly used technology to establish an encrypted HTTP connection? A. the HTTP/1.1 Upgrade header
B. the HTTP/1.0 Upgrade header
C. Secure Hypertext Transfer Protocol
D. HTTPS Answer: D QUESTION 24
What functionality is provided by DNSSEC? A. origin authentication of DNS data
B. data confidentiality of DNS queries and answers
C. access restriction of DNS zone transfers
D. storage of the certificate records in a DNS zone file Answer: A QUESTION 25
What are the two mechanism that are used to authenticate OSPFv3 packets?(Choose two) A. MD5
B. ESP
C. PLAIN TEXT
D. AH
E. SHA Answer: BD QUESTION 26
You have been asked to configure a Cisco ASA appliance in multiple mode with these settings: (A) You need two customer contexts, named contextA and contextB
(B) Allocate interfaces G0/0 and G0/1 to contextA
(C) Allocate interfaces G0/0 and G0/2 to contextB
(D) The physical interface name for G0/1 within contextA should be "inside".
(E) All other context interfaces must be viewable via their physical interface names. If the admin context is already defined and all interfaces are enabled, which command set will complete this configuration? A. context contextA
config-url disk0:/contextA.cfg
allocate-interface GigabitEthernet0/0 visible
allocate-interface GigabitEthernet0/1 inside
context contextB
config-url disk0:/contextB.cfg
allocate-interface GigabitEthernet0/0 visible
allocate-interface GigabitEthernet0/2 visible
B. context contexta
config-url disk0:/contextA.cfg
allocate-interface GigabitEthernet0/0 visible
allocate-interface GigabitEthernet0/1 inside
context contextb
config-url disk0:/contextB.cfg
allocate-interface GigabitEthernet0/0 visible
allocate-interface GigabitEthernet0/2 visible
C. context contextA
config-url disk0:/contextA.cfg
allocate-interface GigabitEthernet0/0 invisible
allocate-interface GigabitEthernet0/1 inside
context contextB
config-url disk0:/contextB.cfg
allocate-interface GigabitEthernet0/0 invisible
allocate-interface GigabitEthernet0/2 invisible
D. context contextA
config-url disk0:/contextA.cfg
allocate-interface GigabitEthernet0/0
allocate-interface GigabitEthernet0/1 inside
context contextB
config-url disk0:/contextB.cfg
allocate-interface GigabitEthernet0/0
allocate-interface GigabitEthernet0/2
E. context contextA
config-url disk0:/contextA.cfg
allocate-interface GigabitEthernet0/0 visible
allocate-interface GigabitEthernet0/1 inside
context contextB
config-url disk0:/contextB.cfg
allocate-interface GigabitEthernet0/1 visible
allocate-interface GigabitEthernet0/2 visible Answer: A QUESTION 27
Which statement about the cisco anyconnect web security module is true ? A. It is VPN client software that works over the SSl protocol.
B. It is an endpoint component that is used with smart tunnel in a clientless SSL VPN.
C. It operates as an NAC agent when it is configured with the Anyconnect VPN client.
D. It is deployed on endpoints to route HTTP traffic to SCANsafe Answer: D QUESTION 28
Which two statements about the SeND protocol are true? (Choose two) A. It uses IPsec as a baseline mechanism
B. It supports an autoconfiguration mechanism
C. It must be enabled before you can configure IPv6 addresses
D. It supports numerous custom neighbor discovery messages
E. It counters neighbor discovery threats
F. It logs IPv6-related threats to an external log server Answer: BE QUESTION 29
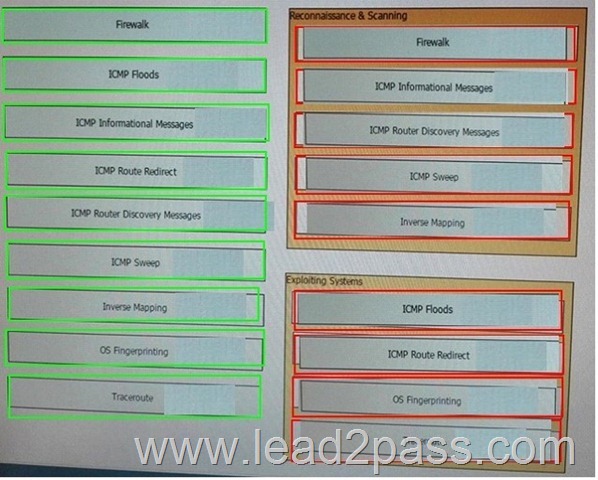
Drag and Drop Question
Drag each attack type on the left to the matching attack category on the right. 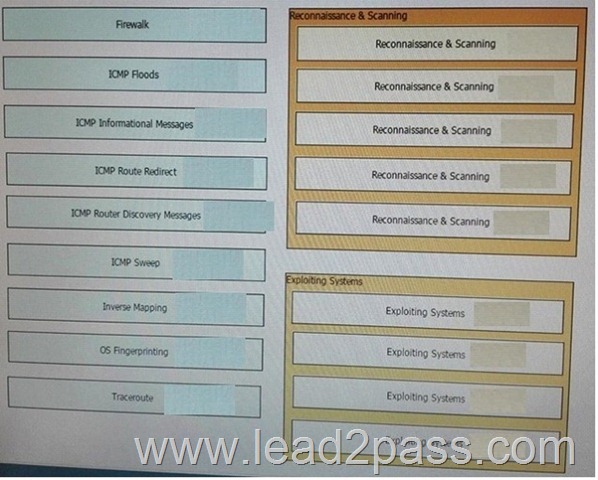
Answer:
 QUESTION 30
Refer to the exhibit. You executed the show crypto key mypubkey rsa command to verify that the RSA key is protected and it generated the given output.
What command must you have entered to protect the key? 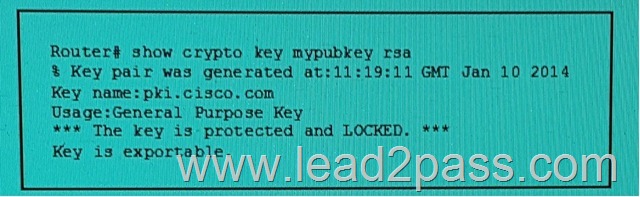
A. crypto key decrypt rsa name pki.cisco.com passphrase CiscoPKI
B. crypto key zeroize rsa CiscoPKI
C. crypto key export ras pki.cisco.com pem url flash: 3des CiscoPKI
D. crypto key lock rsa name pki.cisco.com passphrase CiscoPKI
E. crypto key import rsa pki.cisco.com pem url nvram: CiscoPKI Answer: D QUESTION 31
Refer to the exhibit. What is the effect of the given command sequence? 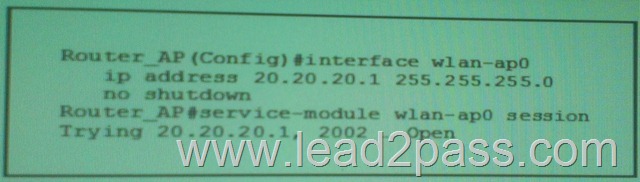
A. The HTTP server and client will negotiate the cipher suite encryption parameters.
B. The server will accept secure HTTP connections from clients with signed security certificates.
C. The client profile will match the authorization profile defined in the AAA server.
D. The clients are added to the cipher suite's profile.
E. The server will accept secure HTTP connections form clients defined in the AAA server. Answer: B QUESTION 32
In ISO 27002, access control code of practice for information Security Management servers which of the following objective? A. Implement protocol control of user, network and application access
B. Optimize the audit process
C. Prevent the physical damage of the resources
D. Educating employees on security requirements and issues Answer: A QUESTION 33
Which two options are differences between a automation and orchestration? (Choose two) A. Automation is an IT workflow composed of tasks, and orchestration is a technical task.
B. Orchestration is focused on multiple technologies to be integrated together.
C. Orchestration is focused on an end-to-end process or workflow
D. Automation is to be used to replace human intervention.
E. Automation is focused on automating a single or multiple tasks. Answer: BC QUESTION 34
What is the first step in performing a risk assessment? A. Identifying critical services and network vulnerabilities and determining the potential impact of their compromise or failure.
B. Investigating reports of data theft or security breaches and assigning responsibility.
C. Terminating any employee believed to be responsible for compromising security.
D. Evaluating the effectiveness and appropriateness of the organization's current risk-management activities.
E. Establishing a security team to perform forensic examinations of previous known attacks. Answer: A QUESTION 35
Which description of a virtual private cloud is true? A. An on-demand configurable pool of shared software applications allocated within a public cloud environment, which provides tenant isolation
B. An on-demand configurable pool of shared data resources allocated within a private cloud environment, which provides assigned DMZ zones
C. An on-demand configurable pool of shared networking resources allocated within a private cloud environment, which provides tenant isolation
D. An on-demand configurable pool of shared computing resources allocated within a public cloud environment, which provides tenant isolation Answer: D QUESTION 36
On which two protocols is VNC based? (Choose two) A. Rdesktop
B. UDP
C. RFB
D. Terminal Services Client
E. CoRD
F. TCP Answer: CF QUESTION 37
How can the tail drop algorithem support traffic when the queue is filled? A. It drop older packet with a size of 64 byts or more until queue has more traffic
B. It drop older packet with a size of less than 64 byts until queue has more traffic
C. It drops all new packets until the queue has room for more traffic
D. It drops older TCP packets that are set to be redelivered due to error on the link until the queue has room for more traffic. Answer: C QUESTION 38
Drag and Drop Question
Drag each step in the cisco PRIST response to incidents and vulnerability involving cisco product on the left into the correct order on the right. 
Answer: 
QUESTION 39
Which two statements about the 3DES encryption protocol are true? (Choose two) A. It can operate in the Electronic Code Book and Asymmetric Block Chaining modes.
B. Its effective key length is 168 bits.
C. It encrypts and decrypts data in three 64-bit blocks with an overall key length of 192 bits.
D. The algorithm is most efficient when it is implemented in software instead of hardware.
E. It encrypts and decrypts data in three 56-bit blocks with an overall key length of 168 bits.
F. Its effective key length is 112 bits. Answer: EF QUESTION 40
You want to enable users in your company's branch offices to deploy their own access points using WAN link from the central office, but you are unable to a deploy a controller in the branch offices. What lightweight access point wireless mode should you choose? A. TLS mode
B. H-REAP mode
C. Monitor mode
D. REAP mode
E. Local mode Answer: B Lead2pass is now offering Lead2pass 400-251 PDF dumps with 100% passing guarantee. Use Lead2pass 400-251 PDF and pass your exam easily. Download Cisco 400-251 exam dumps and prepare for exam. 400-251 new questions on Google Drive: https://drive.google.com/open?id=0B3Syig5i8gpDbkNSWnpMam9TWWM 2017 Cisco 400-251 exam dumps (All 336 Q&As) from Lead2pass: http://www.lead2pass.com/400-251.html [100% Exam Pass Guaranteed]
|






