[Full Version] 100% Pass 400-251 Exam By Training Lead2pass New VCE And PDF Dumps (121-140)
2017 February Cisco Official New Released 400-251 Dumps in Lead2pass.com! 100% Free Download! 100% Pass Guaranteed! Lead2pass provides 100% pass 400-251 exam questions and answers for your Cisco 400-251 exam. We provide Cisco 400-251 exam questions from Lead2pass dumps and answers for the training of 400-251 practice test. Following questions and answers are all new published by Cisco Official Exam Center: http://www.lead2pass.com/400-251.html 3 1 QUESTION 121
The computer at 10.10.10.4 on your network has been infected by a botnet that directs traffic to a malware site at 168.65.201.120. Assuming that filtering will be performed on a Cisco ASA.
What command can you use to block all current and future connections from the infected host? A. ip access-list extended BLOCK_BOT_OUT deny ip any host 10.10.10.4
B. shun 10.10.10.4 168.65.201.120 6000 80
C. ip access-list extended BLOCK_BOT_OUT deny ip host 10.10.10.4 host 168.65.201.120
D. ip access-list extended BLOCK_BOT_OUT deny ip host 168.65.201.120 host 10.10.10.4
E. shun 168.65.201.120 10.10.10.4 6000 80 
Answer: C QUESTION 122
IKEv2 provide greater network attack resiliency against a DoS attack than IKEv1 by utilizing which two functionalities?(Choose two) A. with cookie challenge IKEv2 does not track the state of the initiator until the initiator respond with cookie.
B. Ikev2 perform TCP intercept on all secure connections
C. IKEv2 only allows symmetric keys for peer authentication
D. IKEv2 interoperates with IKEv1 to increase security in IKEv1
E. IKEv2 only allows certificates for peer authentication
F. An IKEv2 responder does not initiate a DH exchange until the initiator responds with a cookie Answer: AF QUESTION 123
Which five of these are criteria for rule-based rogue classification of access points by the cisco Wireless LAN controller? (Choose five) A. MAC address range
B. MAC address range number of clients it has
C. open authentication
D. whether it matches a user-configured SSID
E. whether it operates on an authorized channel
F. minimum RSSI
G. time of day the rogue operates
H. Whether it matches a managed AP SSID Answer: BCDFH QUESTION 124
Which two statement about the DES algorithm are true?(Choose two) A. It uses a 64-bit key block size and its effective key length is 65 bits
B. It uses a 64-bits key block size and its effective key length is 56 bits
C. It is a stream cripher that can be used with any size input
D. It is more efficient in software implements than hardware implementations.
E. It is vulnerable to differential and linear cryptanalysis
F. It is resistant to square attacks Answer: BE QUESTION 125
Which three types of addresses can the Botnet Traffic Filter feature of the Cisco ASA monitor? (Choose three) 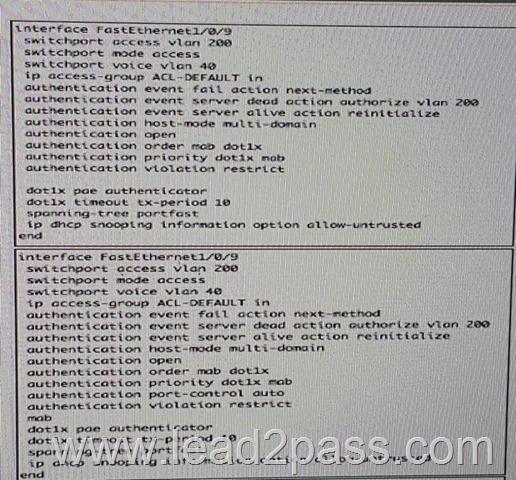
A. Ambiguous addresses
B. Known malware addresses
C. Listed addresses
D. Dynamic addresses
E. Internal addresses
F. Known allowed addresses Answer: ABF QUESTION 126
Which Three statement about cisco IPS manager express are true? (Choose three) A. It provides a customizable view of events statistics.
B. It Can provision policies based on risk rating.
C. It Can provision policies based on signatures.
D. It Can provision policies based on IP addresses and ports.
E. It uses vulnerability-focused signature to protect against zero-day attacks.
F. It supports up to 10 sensors. Answer: ABF QUESTION 127
In Cisco Wireless LAN Controller (WLC. which web policy enables failed Layer 2 authentication to fall back to WebAuth authentication with a user name and password? A. On MAC Filter Failure
B. Pass through
C. Splash Page Web Redirect
D. Conditional Web Redirect
E. Authentication Answer: A QUESTION 128
Drag and Drop Question
Drag and drop each syslog facility code on the left onto its description on the right. 
Answer: 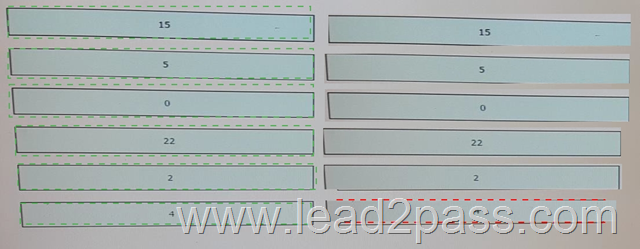
QUESTION 129
Refer to the exhibit. What is the effect of the given configuration? 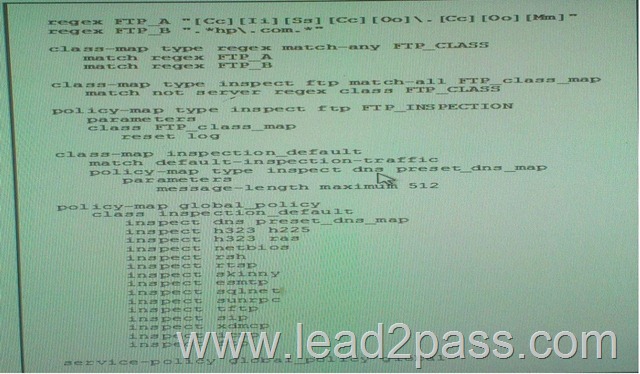
A. It reset and logs FTP connection to all sites except cisco.com and hp.com.
B. FTP connections are unaffected.
C. It resets FTP connection to all sites except cisco.com and hp.com.
D. It resets and logs FTP connection to cisco.com and hp.com only.
E. It resets FPT connection to cisco.com and hp.com only Answer: A QUESTION 130
What port has IANA assigned to the GDOI protocol ? A. UDP 4500
B. UDP 1812
C. UDP 500
D. UDP 848 Answer: D QUESTION 131
Refer to the exhibit, after you implement ingress filter 101 to deny all icmp traffic on your perimeter router user complained of poor web performance and the router and the router display increase CPU load. The debug ipicmp command returned the given output.
Which configuration you make to the router configuration to correct the problem? 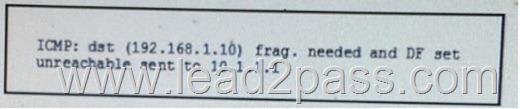
A.
B.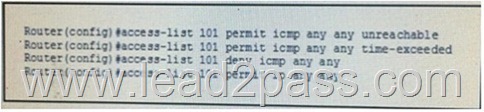
C.
D. Answer: D QUESTION 132
Which two statements about implementing GDOI in a DMVPN network are true?(Choose true) A. Direct spoke-to-spoke traffic is black-holed.
B. Rekeying requires an exclusive IGMP join in the mGRE interface
C. The crypto map is applied to the sub interface of each spoke.
D. If a group member rekey operation fails, it must wait for the SA lifetime to expire before it can reregister with the key server.
E. The DMVPN hub can act as the GDOI key server.
F. DMVPN spokes with tunnel protection allow traffic to be encrypted to the hub Answer: DE QUESTION 133
For which two reasons BVI is required in the Transparent Cisco IOS Firewall? (Choose two) A. BVI is required for the inspection of IP traffic.
B. The firewall can perform routing on bridged interfaces.
C. BVI is required if routing is disabled on the firewall.
D. BVI is required if more than two interfaces are in a bridge group.
E. BVI is required for the inspection of non-IP traffic.
F. BVI can manage the device without having an interface that is configured for routing. Answer: DF QUESTION 134
Drag and Drop Question
Drag each step in the configuration of a cisco ASA NSEL export to a NETFLOW collector on the left into the correct order of operations on the right. 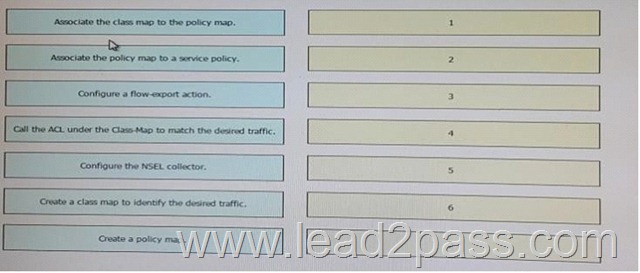
Answer: 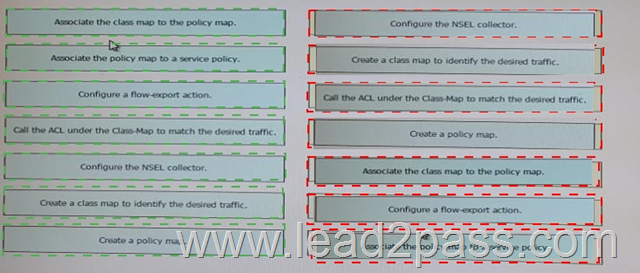
QUESTION 135
Which two u.s government entities are authorized to execute and enforce the penalties for violations of the Sarbanes-oxley(SOX) act? (Choose two) A. Federal trade commission (FTC.
B. internal Revenue service (IRS)
C. Office of Civil Rights (OCR)
D. federal reserve board
E. Securities and exchange commission (SEC.
F. United states Citizenship and immigration services (USCIS) Answer: DE QUESTION 136
MWhich three are RFC 5735 addresses? (Choose three.) A. 171.10.0.0/24
B. 0.0.0.0/8
C. 203.0.113.0/24
D. 192.80.90.0/24
E. 172.16.0.0/12
F. 198.50.100.0/24 Answer: BCE QUESTION 137
Refer to the exhibit . Which Statement about this configuration is true? 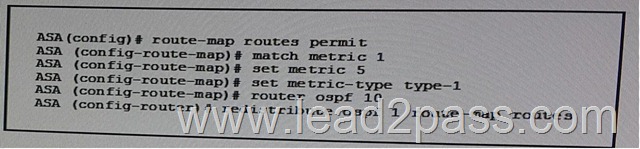
A. The ASA stops LSA type 7 packets from flooding into OSPF area 1.
B. The ASA injects a static default route into OSPF area 1.
C. The ASA redistributes routes from one OSPF process to another.
D. The ASA redistributes routes from one routing protocol to another.
E. The ASA injects a static default route into OSPF process 1. Answer: C QUESTION 138
Drag and Drop Question
Drag and drop step in the flow of packets on a DMVPN network using GDOI on the left into the correct sequence on the right 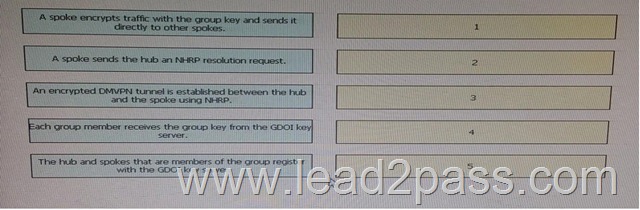
Answer: 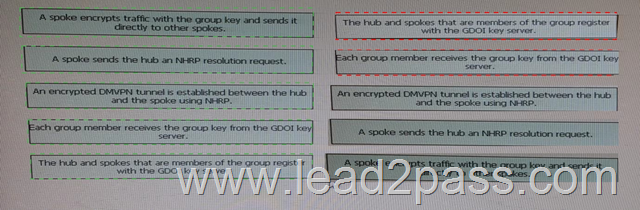
QUESTION 139
When attempting to use basic Http authentication to authenticate a client,which type of HTTP massage should the server use? A. HTTP 200 with a WWW-authenticate header.
B. HTTP 401 with a WWW-authenticate header.
C. Http 302 with an authenticate header.
D. HTTP 407. Answer: B QUESTION 140
Drag and Drop Question
Drag and Drop each Cisco Intrusion Prevention System anomaly detection event action on the left onto the matching description on the right. 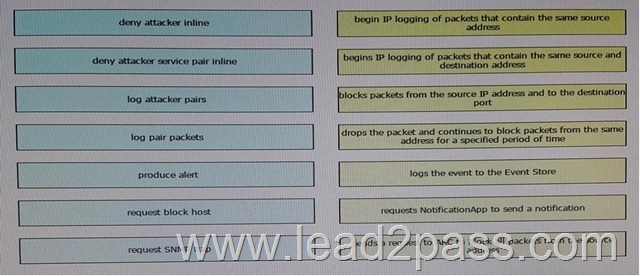
Answer: 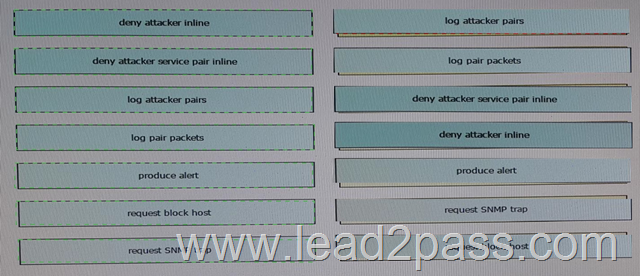
Lead2pass is the leader in 400-251 certification test questions with training materials for Cisco 400-251 exam dumps. Lead2pass Cisco training tools are constantly being revised and updated. We 100% guarantee Cisco 400-251 exam questions with quality and reliability which will help you pass Cisco 400-251 exam. 400-251 new questions on Google Drive: https://drive.google.com/open?id=0B3Syig5i8gpDbkNSWnpMam9TWWM 2 2017 Cisco 400-251 exam dumps (All 336 Q&As) from Lead2pass: http://www.lead2pass.com/400-251.html 3 1 [100% Exam Pass Guaranteed]
|
















